
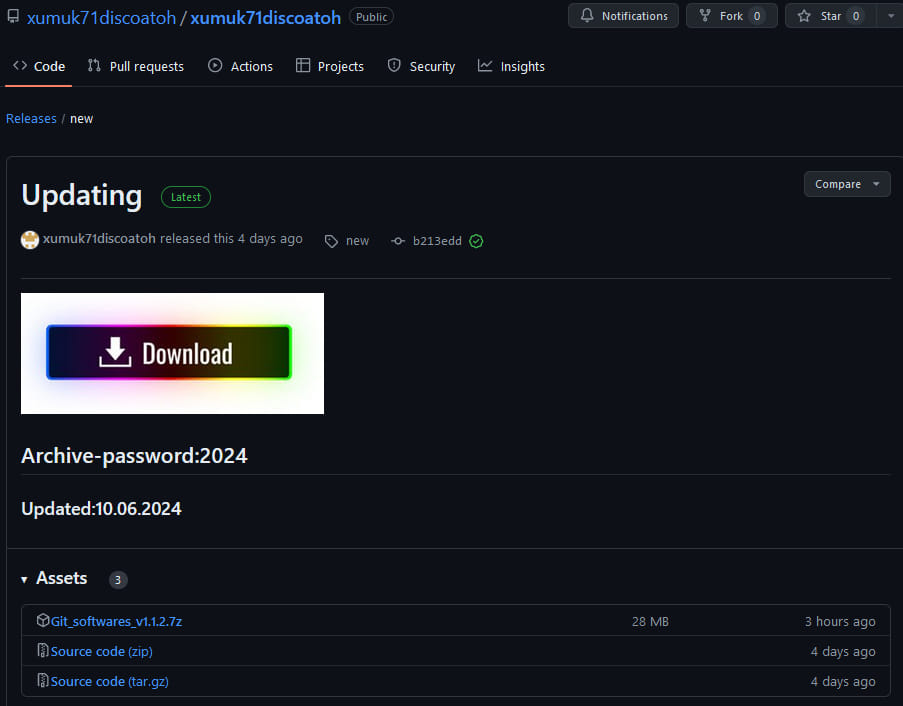
Risk actors often known as ‘Stargazer Goblin’ have created a malware Distribution-as-a-Service (DaaS) from over 3,000 faux accounts on GitHub that push information-stealing malware.
The malware supply service is named Stargazers Ghost Community and it makes use of GitHub repositories together with compromised WordPress websites to distribute password-protected archives that include malware. Normally, the malware are infostealers, reminiscent of RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer.
Supply: Examine Level
As a result of GitHub being a well known, trusted service, folks deal with it with much less suspicion and could also be extra more likely to click on on hyperlinks they discover within the service’s repositories.
Examine Level Analysis found the operation, which says it’s the first time that such an organized and large-scale scheme has been documented operating on GitHub.
“The campaigns carried out by the Stargazers Ghost Community and malware distributed by way of this service are extraordinarily profitable,” explains the report by Examine Level Analysis.
“In a brief time frame, 1000’s of victims put in software program from what seems to be a respectable repository with out suspecting any malicious intent. The closely victim-oriented phishing templates enable risk actors to contaminate victims with particular profiles and on-line accounts, making the infections much more invaluable.”
GitHub ‘ghosts’ spreading malware
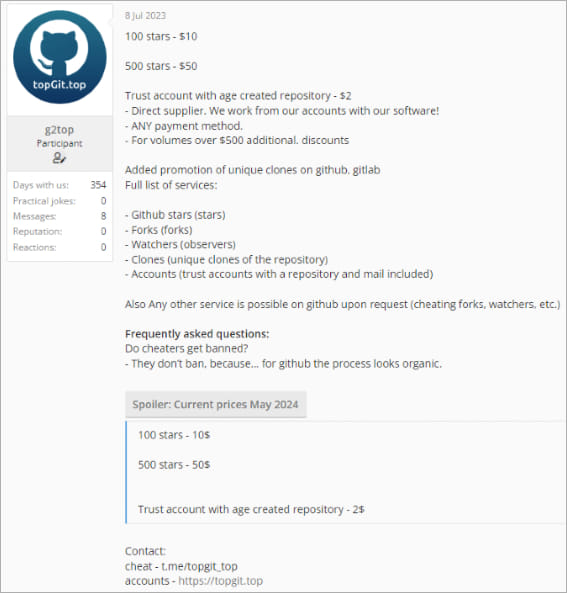
The creator of the DaaS operation, Stargazer Goblin, has been actively selling the malware distribution service on the darkish internet since June 2023. Nevertheless, Examine Level says there’s proof it has been lively since August 2022.
Supply: Examine Level
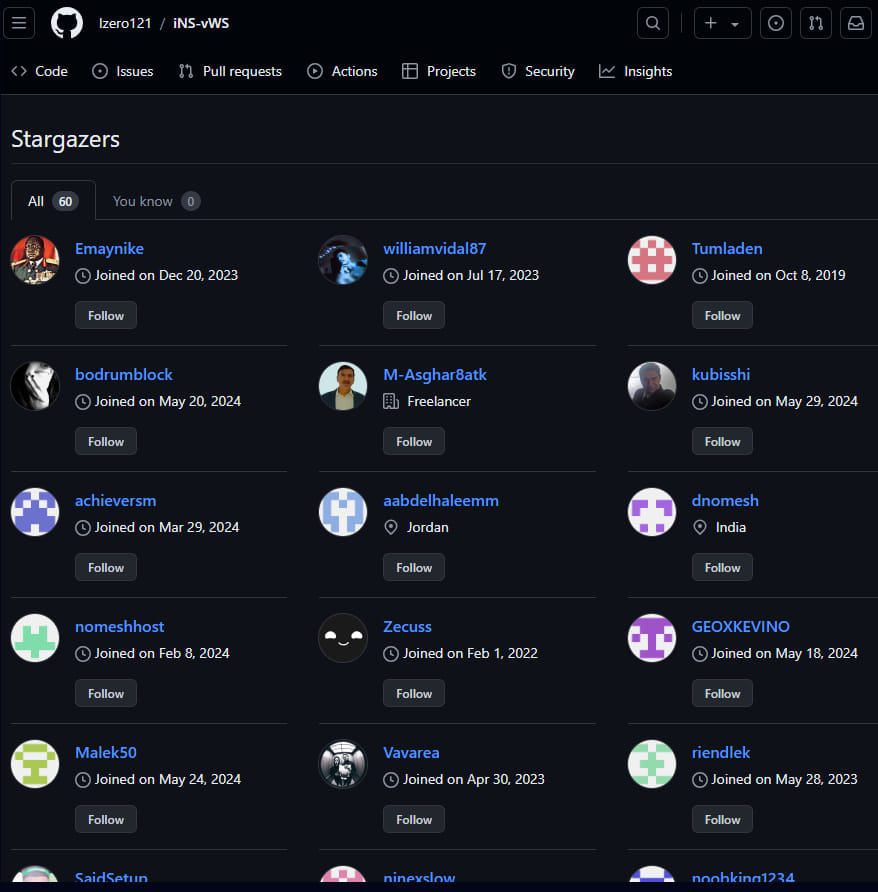
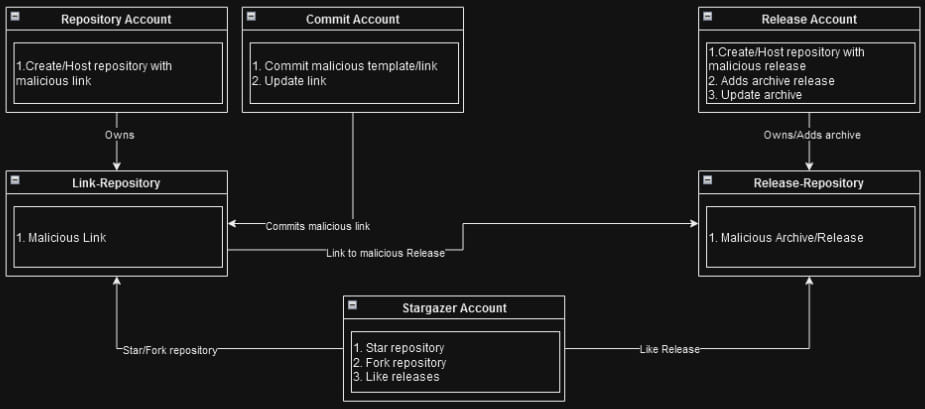
Stargazer Goblin established a system the place they create a whole lot of repositories utilizing three thousand faux ‘ghost’ accounts. These accounts star, fork, and subscribe to malicious repositories to extend their obvious legitimacy and make them extra more likely to seem on GitHub’s trending part.
Supply: Examine Level
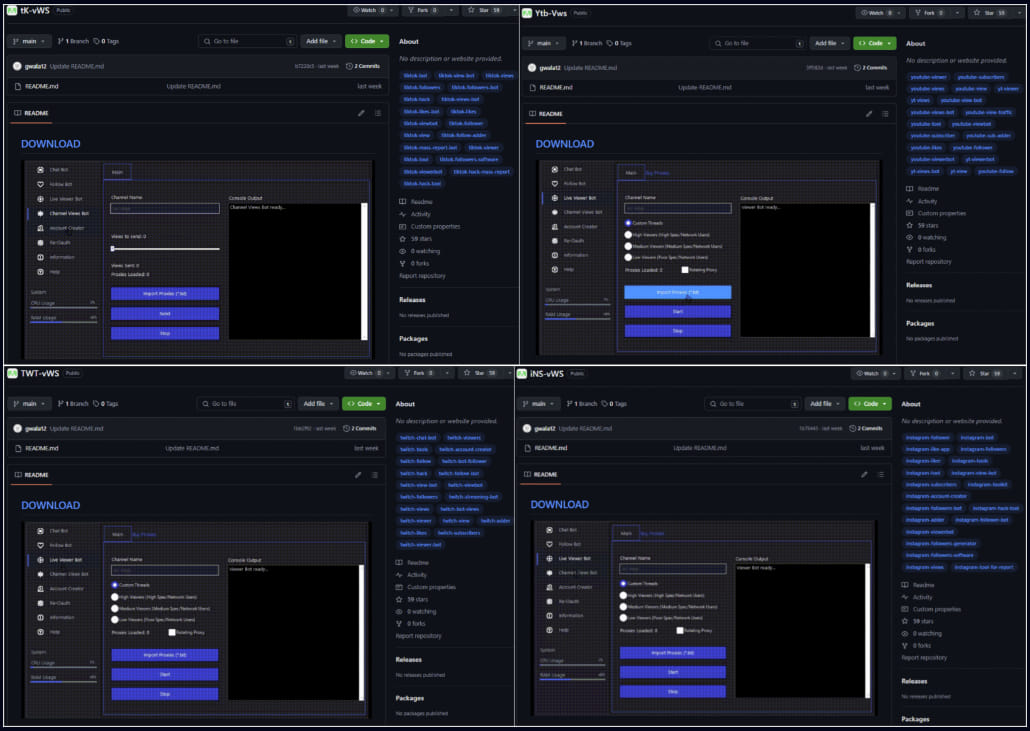
The repositories use challenge names and tags that focus on particular pursuits like cryptocurrency, gaming, and social media.
Supply: Examine Level
The ‘ghost’ accounts are assigned distinct roles. One group serves the phishing template, one other offers the phishing picture, and a 3rd serves the malware, which supplies the scheme a sure stage of operational resilience.
“The third account, which serves the malware, is extra more likely to be detected. When this occurs, GitHub bans all the account, repository, and related releases,” explains researcher Antonis Terefos.
“In response to such actions, Stargazer Goblin updates the primary account’s phishing repository with a brand new hyperlink to a brand new lively malicious launch. This permits the community to proceed working with minimal losses when a malware-serving account is banned.”
Supply: Examine Level
Examine Level has noticed a case of a YouTube video with a software program tutorial linking to the identical operative as in one of many ‘Stargazers Ghost Community’ GitHub repositories.
The researchers be aware that it could possibly be one of many probably a number of examples of channels used to funnel site visitors to phishing repositories or malware distribution websites.
By way of the scale of the operation and its revenue era, Examine Level estimates that the risk actor has remodeled $100,000 for the reason that service’s launch.
As for what malware is distributed by the Stargazers Ghost Community’s operation, Examine Level says it consists of RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer, amongst others.
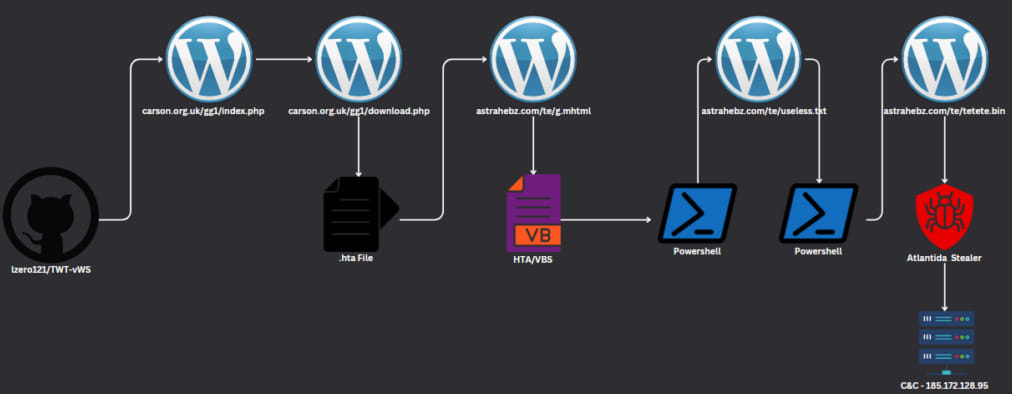
In a single instance assault chain introduced in Examine Level’s report, the GitHub repository redirects guests to a compromised WordPress web site, from the place they obtain a ZIP archive containing an HTA file with VBScript.
Supply: Examine Level
The VBScript triggers the execution of two successive PowerShell scripts that in the end result in the deployment of the Atlantida Stealer.
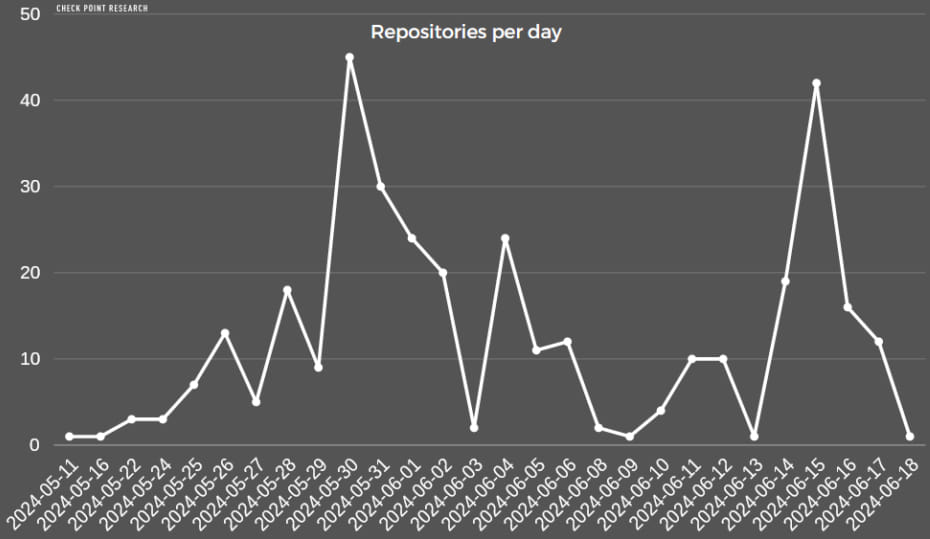
Though GitHub has taken motion towards lots of the malicious and basically faux repositories, taking down over 1,500 since Might 2024, Examine Level says that over 200 are at present lively and proceed to distribute malware.
Supply: Examine Level
Customers arriving on GitHub repositories by malvertising, Google Search outcomes, YouTube movies, Telegram, or social media are suggested to be very cautious with file downloads and the URLs they click on.
That is very true of password-protected archives, which can’t be scanned by antivirus software program. For these kind of recordsdata, it’s instructed you extract them on a VM and scan the extracted contents with antivirus software program to test for malware.
If a digital machine shouldn’t be obtainable, it’s also possible to use VirusTotal, which is able to immediate for the password of a protected archive so it might scan its contents. Nevertheless, VirusTotal can solely scan a protected archive if it incorporates a single file.


