
A beforehand undocumented ransomware payload named NailaoLocker has been noticed in assaults concentrating on European healthcare organizations between June and October 2024.
The assaults exploited CVE-2024-24919, a Test Level Safety Gateway vulnerability, to realize entry to focused networks and deploy the ShadowPad and PlugX malware, two households tightly related to Chinese language state-sponsored risk teams.
Orange Cyberdefense CERT hyperlinks the assaults to Chinese language cyber-espionage techniques, although there’s not sufficient proof to attribute them to particular teams.
NailaoLocker particulars
Orange’s researchers report that NailaoLocker is a comparatively unsophisticated ransomware pressure in comparison with essentially the most distinguished households within the area.
The rationale why Orange sees NailaoLocker as a moderately primary ransomware is that, it doesn’t terminate safety processes or operating companies, it lacks anti-debugging and sandbox evasion mechanisms, and doesn’t scan community shares.
“Written in C++, NailaoLocker is comparatively unsophisticated and poorly designed, seemingly not supposed to ensure full encryption,” mentions Orange.
The malware is deployed on the right track techniques through DLL sideloading (sensapi.dll) involving a official and signed executable (usysdiag.exe).
The malware loader (NailaoLoader) verifies the atmosphere by performing reminiscence handle checks after which decrypts the primary payload (usysdiag.exe.dat) and masses it into reminiscence.
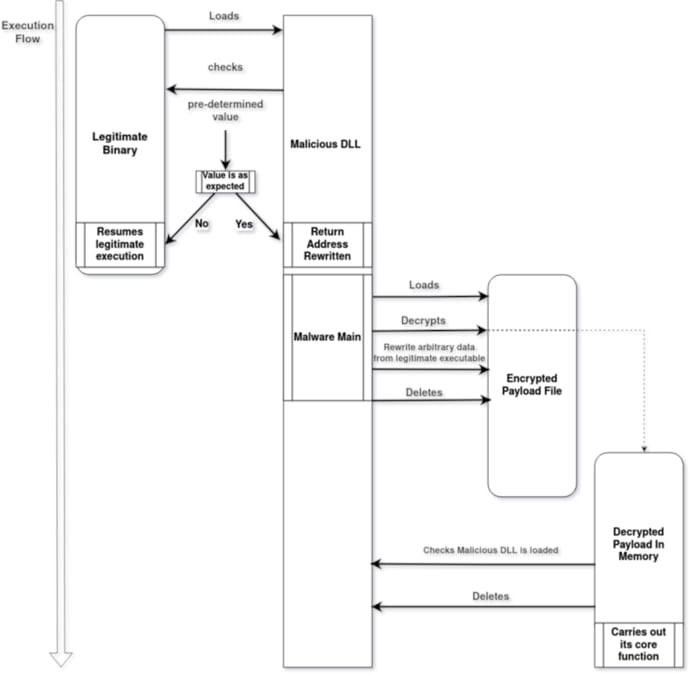
Supply: Orange CERT
Subsequent, the NailaoLocker prompts and begins encrypting recordsdata utilizing an AES-256-CTR scheme, appending the “.locked” extension to encrypted recordsdata.
After the encryption is completed, the ransomware drops an HTML ransom be aware with the very unusually lengthy filename of “unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please.html.”
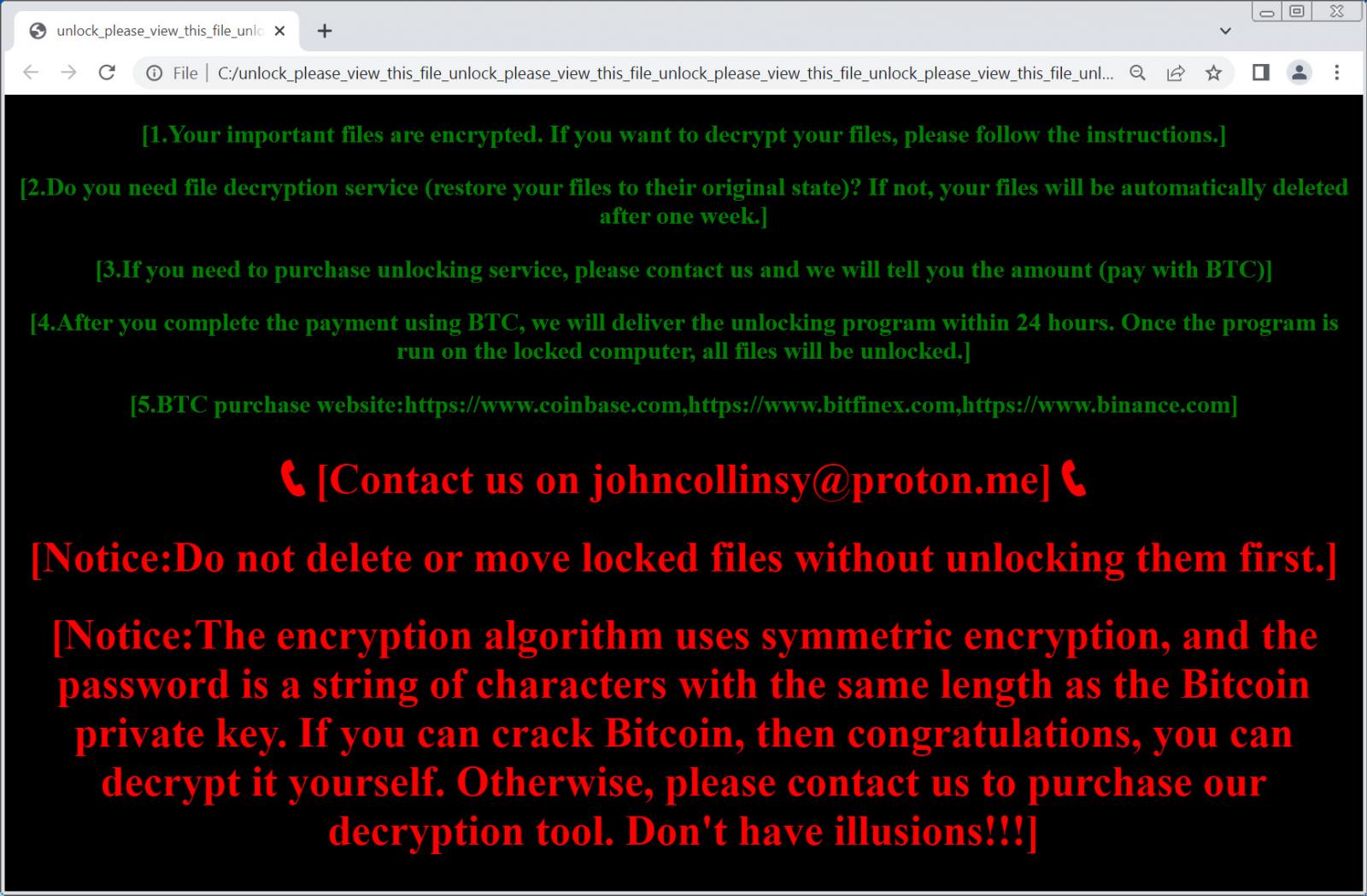
Supply: Orange CERT
This ransom be aware instructs the victims to contact them at a disposable ProtonMail handle, which, in a couple of instances seen by BleepingComputer, was johncollinsy@proton[.]me.
The ransom be aware doesn’t point out that knowledge was stolen, which is odd for many trendy ransomware operations.
Espionage and ransomware mixed
Investigating deeper, Orange says they discovered some overlap between the content material of the ransom be aware and a ransomware instrument offered by a cybercrime group named Kodex Softwares (previously Evil Extractor). Nonetheless, there have been no direct code overlaps, making the connection blurry.
Orange has shared a number of hypotheses for the assaults, together with false flag operations meant to distract, strategic knowledge theft operations doubled with income era, and, extra probably, a Chinese language cyberespionage group “moonlighting” on the facet to earn some cash.
Solely final week, Symantec reported about suspected Emperor Dragonfly (a.ok.a. Bronze Starlight) operatives deploying RA World ransomware towards Asian software program companies and demanding a ransom of $2 million.
In comparison with North Korean actors who’re recognized to pursue a number of objectives in parallel, together with monetary positive aspects through ransomware assaults, Chinese language state-backed actors have not adopted this strategy, so the shift in techniques is regarding.

