
Microsoft has taken down an undisclosed variety of GitHub repositories utilized in a large malvertising marketing campaign that impacted virtually a million units worldwide.
The corporate’s menace analysts detected these assaults in early December 2024 after observing a number of units downloading malware from GitHub repos, malware that was later used to deploy a string of varied different payloads on compromised methods.
After analyzing the marketing campaign, they found that the attackers injected adverts into movies on unlawful pirated streaming web sites that redirect potential victims to malicious GitHub repositories underneath their management.
“The streaming web sites embedded malvertising redirectors inside film frames to generate pay-per-view or pay-per-click income from malvertising platforms,” Microsoft defined at present. “These redirectors subsequently routed site visitors by means of one or two further malicious redirectors, in the end main to a different web site, corresponding to a malware or tech help rip-off web site, which then redirected to GitHub.”
The malvertising movies redirected customers to the GitHub repos that contaminated them with malware designed to carry out system discovery, gather detailed system data (e.g., reminiscence dimension, graphic particulars, display decision, working system (OS), and person paths), and exfiltrate the harvested information whereas deploying further stage-two payloads.
A 3rd-stage PowerShell script payload then downloads the NetSupport distant entry trojan (RAT) from a command-and-control server and establishes persistence within the registry for the RAT. As soon as executed, the malware may also deploy the Lumma info stealer malware and the open-source Doenerium infostealer to exfiltrate person information and browser credentials.
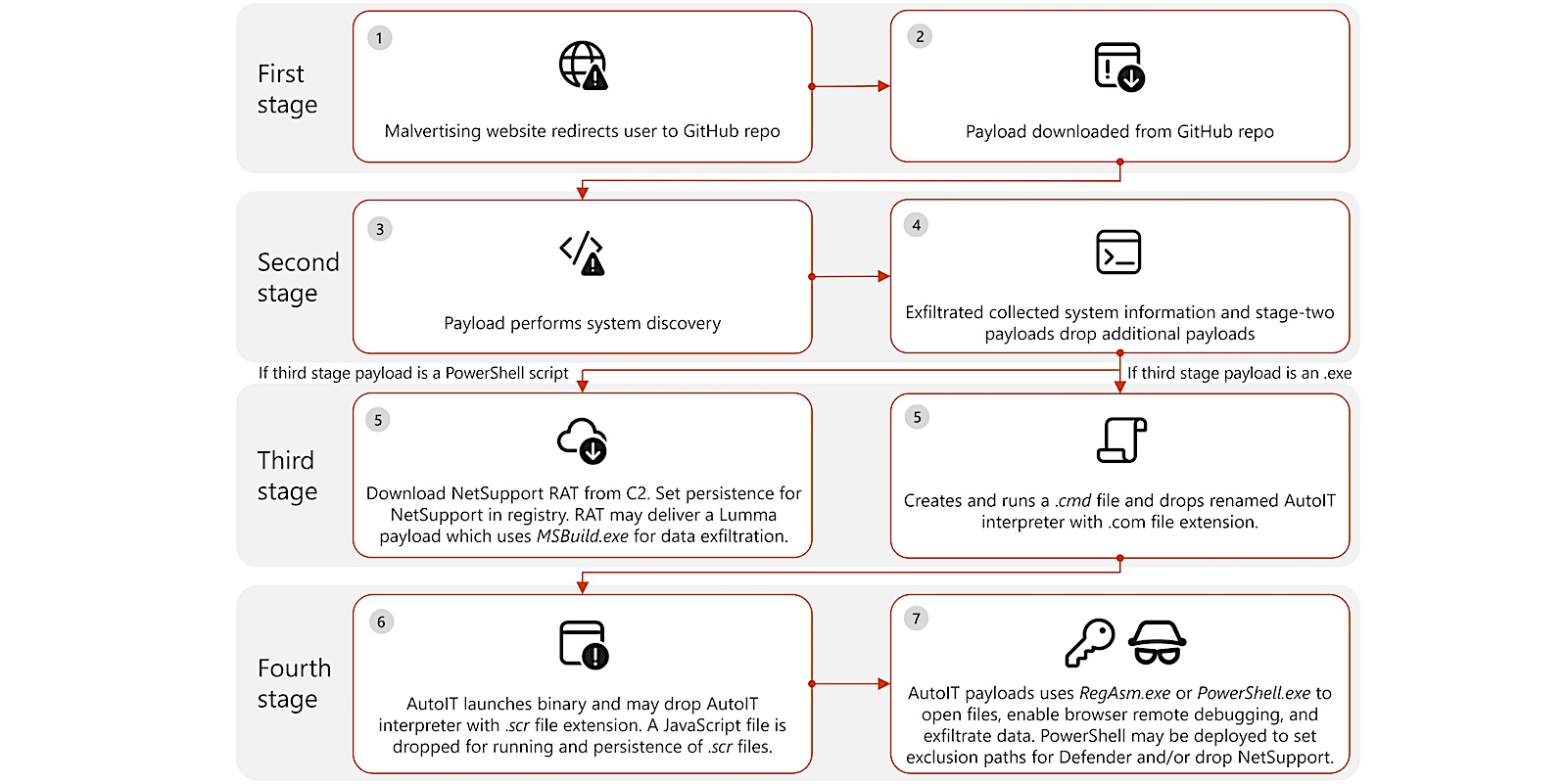
Then again, if the third-stage payload is an executable file, it creates and runs a CMD file whereas dropping a renamed AutoIt interpreter with a .com extension. This AutoIt part then launches the binary and should drop one other model of the AutoIt interpreter with a .scr extension. A JavaScript file can also be deployed to assist execute and achieve persistence for .scr recordsdata.
Within the final stage of the assault, the AutoIt payloads use RegAsm or PowerShell to open recordsdata, allow distant browser debugging, and exfiltrate further info. In some instances, PowerShell can also be used to configure exclusion paths for Home windows Defender or to drop extra NetSupport payloads.
Whereas GitHub was the first platform to host payloads delivered throughout the marketing campaign’s first stage, Microsoft Risk Intelligence additionally noticed payloads hosted on Dropbox and Discord.
“This exercise is tracked underneath the umbrella title Storm-0408 that we use to trace quite a few menace actors related to distant entry or information-stealing malware and who use phishing, search engine marketing (website positioning), or malvertising campaigns to distribute malicious payloads,” Microsoft mentioned.
“The marketing campaign impacted a variety of organizations and industries, together with each client and enterprise units, highlighting the indiscriminate nature of the assault.”
Microsoft’s report supplies further and extra detailed info relating to the assorted levels of the assaults and the payloads used throughout the multi-stage assault chain of this complicated malvertising marketing campaign.

