
Microsoft warns concerning the safety dangers posed by default configurations in Kubernetes deployments, notably these utilizing out-of-the-box Helm charts, which might publicly expose delicate knowledge.
In lots of instances, these Helm charts required no authentication, left exploitable ports open, and used weak or hardcoded passwords that had been trivial to interrupt.
A report revealed by safety researchers Michael Katchinskiy and Yossi Weizman of Microsoft Defender for Cloud Analysis highlights three instances as examples of a broader safety concern that places Kubernetes workloads in danger.
Ease vs safety
Kubernetes is a extensively used open-source platform designed to automate the deployment, scaling, and administration of containerized purposes.
Helm is a bundle supervisor for Kubernetes, and charts are templates/blueprints for deploying apps on the platform, offering YAML recordsdata that outline key assets wanted to run an app.
Helm charts are in style as a result of they simplify and velocity up advanced deployments. Nevertheless, as highlighted in Microsoft’s report, in lots of instances, the default settings in these charts lack correct safety measures.
Customers inexperienced with cloud safety typically deploy these Helm charts as they’re, unintentionally exposing companies to the web and permitting attackers to scan and exploit misconfigured purposes.
Supply: Microsoft
“Default configurations that lack correct safety controls create a extreme safety risk,” warns the Microsoft researchers.
“With out fastidiously reviewing the YAML manifests and Helm charts, organizations could unknowingly deploy companies missing any type of safety, leaving them absolutely uncovered to attackers.”
“That is notably regarding when the deployed utility can question delicate APIs or permit administrative actions, which is precisely what we are going to shortly see.”
The researchers spotlight three instances of Helm charts that put Kubernetes environments susceptible to assaults, summarized as follows.
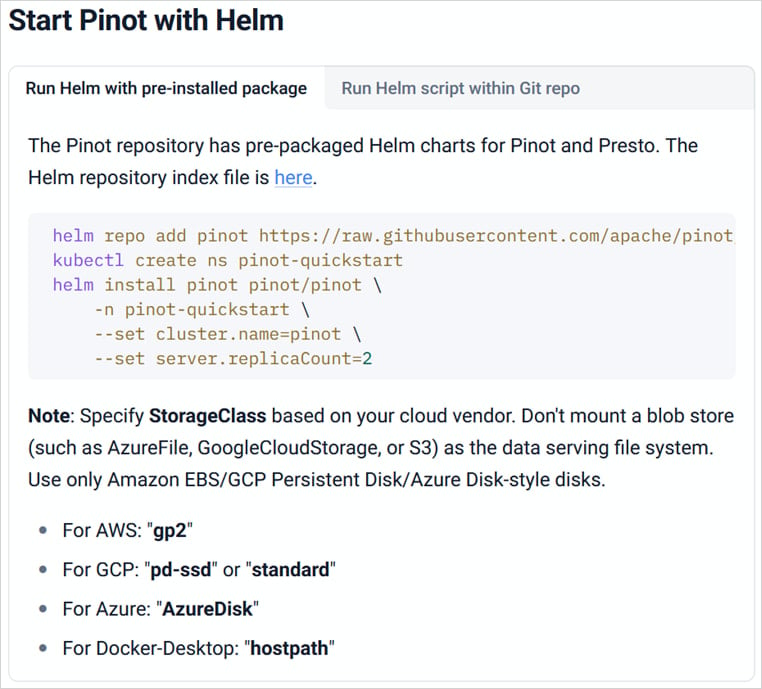
- Apache Pinot: Exposes core companies (pinot-controller and pinot-broker) by way of Kubernetes LoadBalancer companies with none authentication.
- Meshery: Public sign-up is allowed from uncovered IP, permitting anybody to register and acquire entry to cluster operations.
- Selenium Grid: A NodePort exposes the service throughout all nodes in a cluster, relying solely on exterior firewall guidelines for defense. The problem does not affect the official Helm chart, however many extensively referenced GitHub tasks.
Regarding Selenium Grid, Wiz and different cybersecurity corporations have beforehand noticed assaults focusing on misconfigured cases to deploy XMRig miners to mine Monero cryptocurrency.
To mitigate the dangers, Microsoft recommends fastidiously reviewing the default configuration of Helm charts to guage it from a safety perspective, making certain that it consists of authentication and community isolation.
Moreover, it is suggested to carry out common scans for misconfigurations that expose workload interfaces publicly and carefully monitor containers for suspicious exercise.


