
A lately disclosed vulnerability within the Widespread Unix Printing System (CUPS) open-source printing system could be exploited by risk actors to launch distributed denial-of-service (DDoS) assaults with a 600x amplification issue.
As Akamai safety researchers discovered, a CVE-2024-47176 safety flaw within the cups-browsed daemon that may be chained with three different bugs to achieve distant code execution on Unix-like methods by way of a single UDP packet will also be leveraged to amplify DDoS assaults.
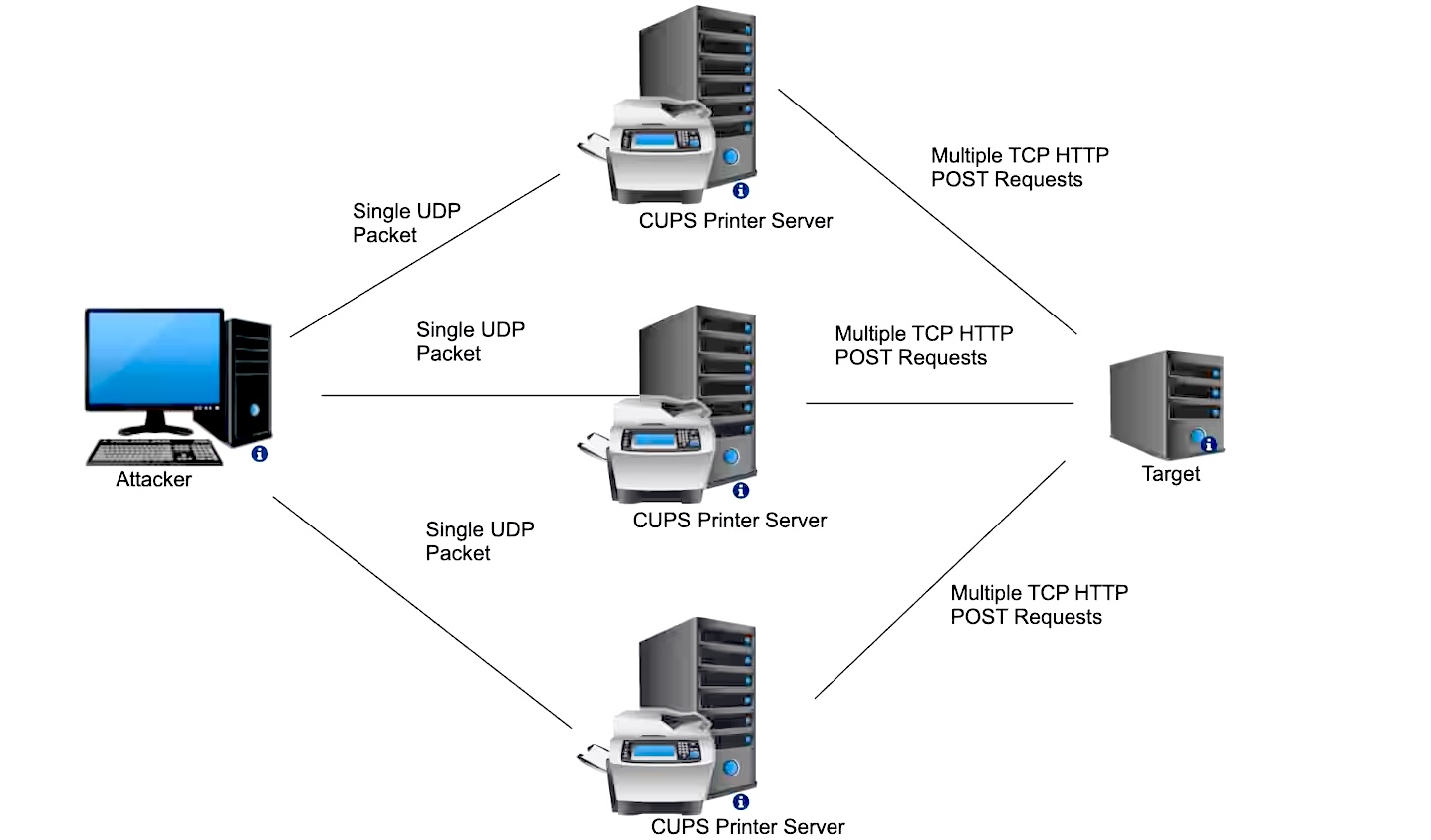
The vulnerability is triggered when an attacker sends a specifically crafted packet, tricking a CUPS server into treating a goal as a printer to be added.
Every packet despatched to susceptible CUPS servers prompts them to generate bigger IPP/HTTP requests geared toward the focused system. This impacts each the goal and the CUPS server, consuming their bandwidth and CPU sources.
Begins with a single malicious UDP packet
To provoke such an assault, a malicious actor solely must ship a single packet to an uncovered and susceptible CUPS service uncovered on-line. Akamai researchers estimate that round 58,000 servers, out of over 198,000 uncovered units, might be recruited for DDoS assaults.
Moreover, a whole bunch of susceptible units demonstrated an “infinite loop” of requests, with some CUPS servers repeatedly sending requests after receiving an preliminary probe and a few servers coming into an limitless loop in response to particular HTTP/404 errors.
Many of those susceptible machines had been operating outdated variations of CUPS (going way back to 2007), that are straightforward targets for cybercriminals who can exploit them to construct botnets by way of the RCE chain or use them for DDoS amplification.
“Within the worst-case state of affairs, we noticed what gave the impression to be an limitless stream of tried connections and requests because of a single probe. These flows seem to haven’t any finish, and can proceed till the daemon is killed or restarted,” the Akamai researchers mentioned.
“Many of those methods we noticed in testing established hundreds of requests, sending them to our testing infrastructure. In some circumstances, this conduct appeared to proceed indefinitely.”
Seconds wanted to drag off an assault
This DDoS amplification assault additionally requires minimal sources and little time to execute. Akamai warns {that a} risk actor might simply take management of each uncovered CUPS service on the web in seconds.
Admins are suggested to deploy CVE-2024-47176 patches or disable the cups-browsed service from operating to dam potential assaults to mitigate the chance of getting their servers added to a botnet or utilized in DDoS assaults.
“DDoS continues to be a viable assault vector used to harass and disrupt victims throughout the web, from main industries and governments to small content material creators, on-line retailers, and avid gamers,” Akamai’s researchers warned.
“Though the unique evaluation centered on the RCE, which might have a extra extreme end result, DDoS amplification can also be simply abused on this case.”
As Cloudflare revealed this week, its DDoS protection methods needed to shield clients in opposition to a wave of hyper-volumetric L3/4 DDoS assaults reaching 3.8 terabits per second (Tbps), the most important such assault ever recorded.

