
Researchers are warning of risk actors more and more abusing the Cloudflare Tunnel service in malware campaigns that normally ship distant entry trojans (RATs).
This cybercriminal exercise was frst detected in February and it’s leveraging the TryCloudflare free service to distribute a number of RATs, together with AsyncRAT, GuLoader, VenomRAT, Remcos RAT, and Xworm.
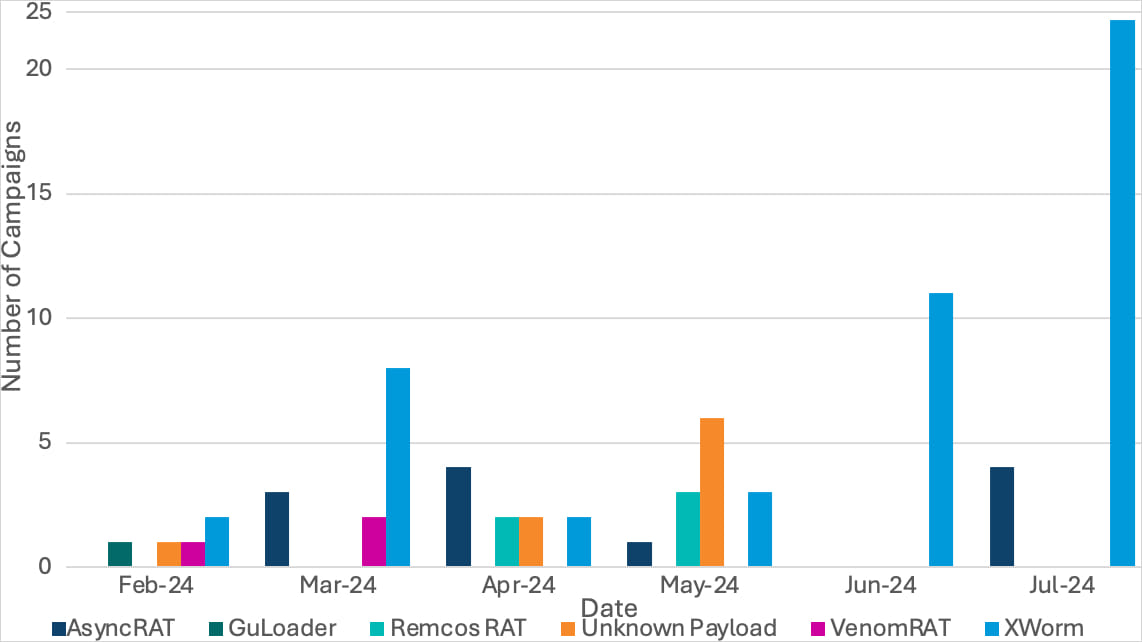
Supply: Proofpoint
The Cloudflare Tunnel service permits proxying site visitors via an encrypted tunnel to entry native providers and servers over the web with out exposing IP addresses. This could include added safety and comfort as a result of there isn’t a have to open any public inbound ports or to arrange VPN connections.
With TryCloudflare, customers can create short-term tunnels to native servers and take a look at the service with out the necessity of a Cloudflare account.
Every tunnel generates a brief random subdomain on the trycloudflare.com area, which is used to route site visitors via Cloudflare’s community to the native server.
Risk actors have abused the function previously to realize distant entry to compromised techniques whereas evading detection.
Newest marketing campaign
In a report at present, cybersecurity firm Proofpoint says that it noticed malware exercise concentrating on legislation, finance, manufacturing, and expertise organizations with malicious .LNK information hosted on the reliable TryCloudflare area.
The risk actors are luring targets with tax-themed emails with URLs or attachments resulting in the LNK payload. When launched, the payload runs BAT or CMD scripts that deploy PowerShell.
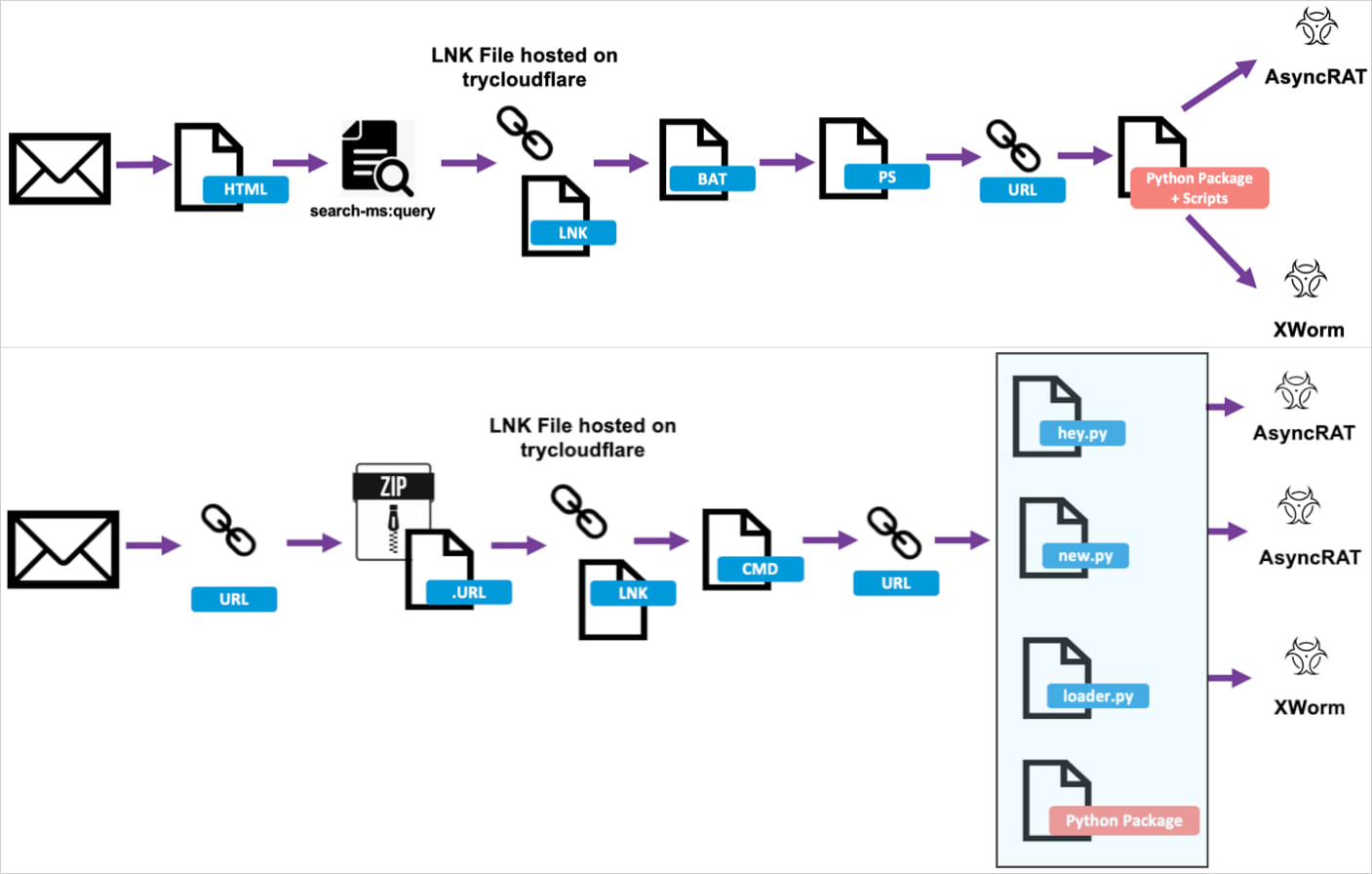
Supply: Proofpoint
Within the ultimate stage of the assault, Python installers are downloaded for the ultimate payload.
Proofpoint experiences that the e-mail distribution wave that began on July 11 has distributed over 1,500 malicious messages, whereas an earlier wave from Could 28 contained lower than 50 messages.
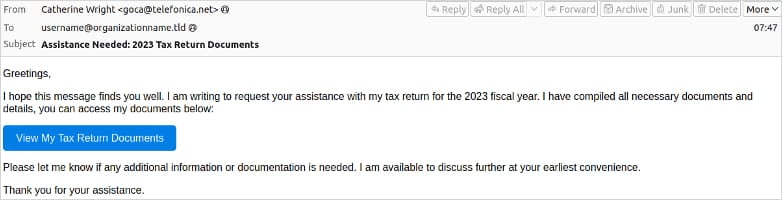
Supply: Proofpoint
Internet hosting LNK information on Cloudflare presents a number of advantages, together with making the site visitors seem reliable as a result of service’s repute.
Furthermore, the TryCloudflare Tunnel function presents anonymity, and the LNK-serving subdomains are short-term, so blocking them doesn’t assist defenders an excessive amount of.
In the end, the service is free and dependable, so the cybercriminals don’t have to cowl the price of organising their very own infrastructure. If automation is employed to evade blocks from Cloudflare, the cybercriminals can abuse these tunnels even for large-scale operations.
BleepingComputer has reached Cloudflare for a touch upon the exercise reported by Proofpoint, and an organization consultant replied with the next assertion:
Cloudflare instantly disables and takes down malicious tunnels as they’re found by our workforce or reported on by third events.
Previously few years, Cloudflare has launched machine studying detections on our tunnel product in an effort to higher comprise malicious exercise which will happen.
We encourage Proofpoint and different safety distributors to submit any suspicious URLs and we are going to take motion towards any clients that use our providers for malware.

