The Gootloader malware loader operation has returned after a 7-month absence and is as soon as once more performing search engine optimisation poisoning to advertise pretend web sites that distribute the malware.
Gootloader is a JavaScript-based malware loader unfold by compromised or attacker-controlled web sites, used to trick customers into downloading malicious paperwork.
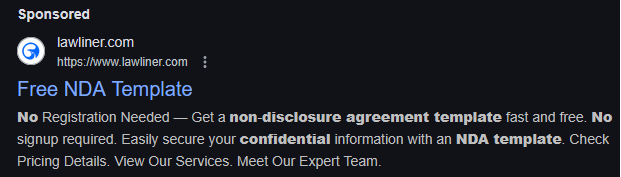
The web sites are promoted in search engines like google and yahoo both through adverts or by SEO (search engine optimisation) poisoning, which ranks an internet site greater within the outcomes for a specific key phrase, like authorized paperwork and agreements.
Supply: Gootloader researcher
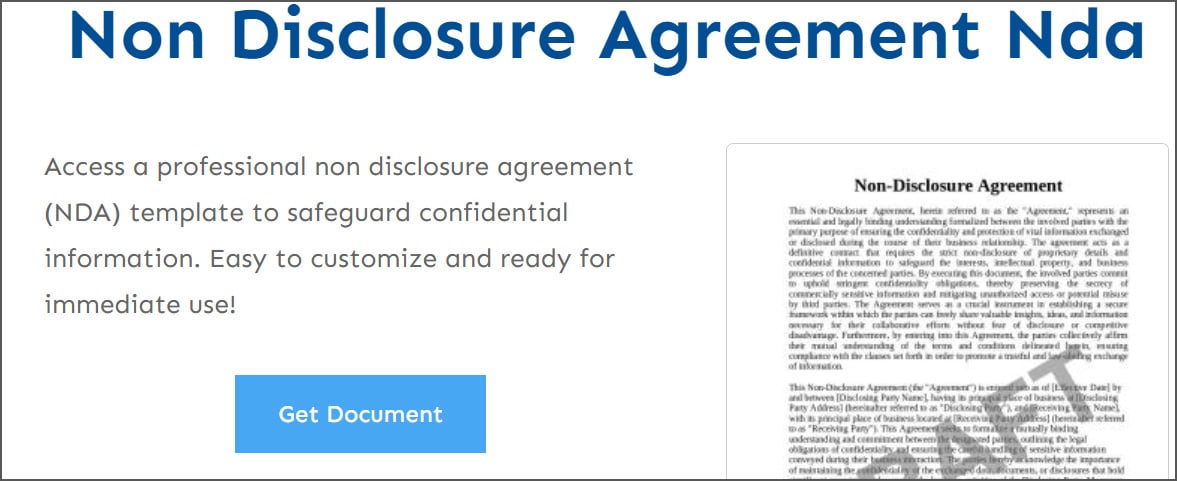
Previously, these web sites would show pretend message boards that pretended to debate customers’ question, with some posts recommending (malicious) doc templates that could possibly be downloaded. The search engine optimisation campaigns later switched to utilizing web sites that fake to supply free templates for varied authorized paperwork.
Supply: Gootloader researcher
When a customer clicked the “Get Doc” button, the location checked in the event that they have been a professional consumer and, in that case, downloaded an archive containing a malicious doc with a .js extension. For instance, the archive might embody a file named mutual_non_disclosure_agreement.js.
Gootloader would execute when launching the doc and downloaded further malware payloads onto the gadget, together with Cobalt Strike, backdoors, and bots that supplied preliminary entry to company networks. Different menace actors then used this entry to deploy ransomware or conduct different assaults.
Gootloader returns
A cybersecurity researcher working below the pseudonym “Gootloader” has been monitoring and actively disrupting the malware operation for years by submitting abuse studies with ISPs and internet hosting platforms to take down attacker-controlled infrastructure.
The researcher informed BleepingComputer that his actions led to the Gootloader operation abruptly ceasing on March thirty first, 2025.
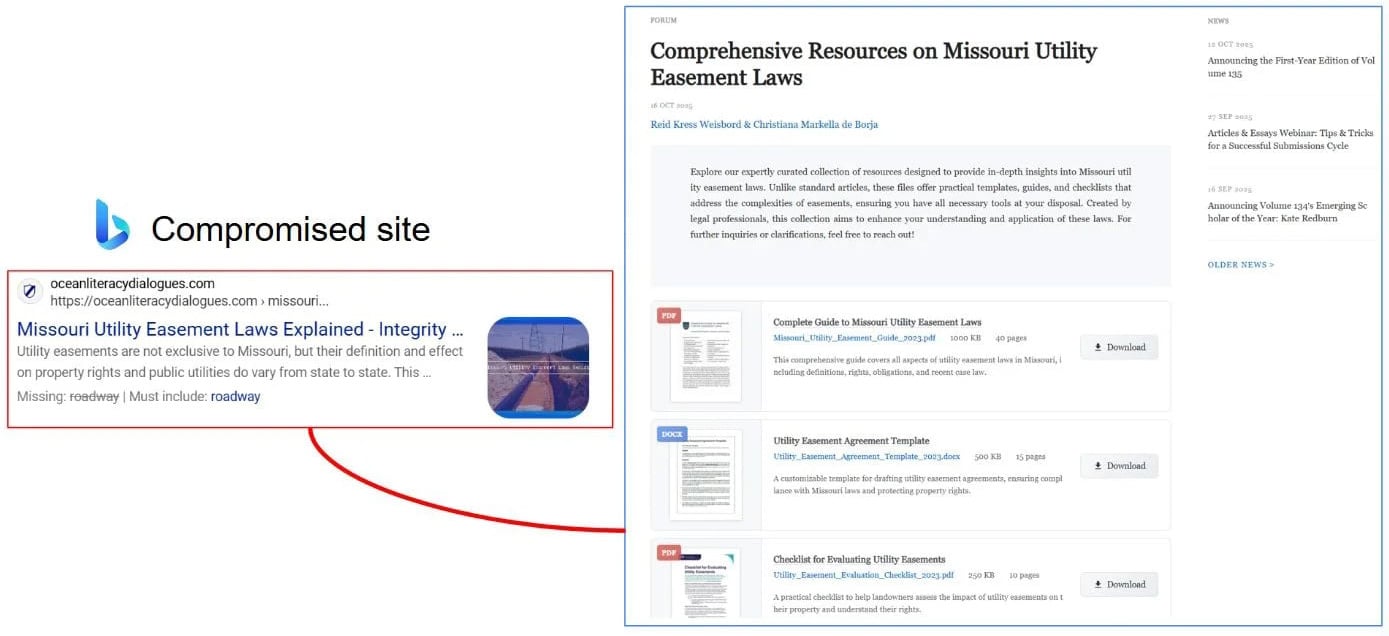
The researcher and Anna Pham of Huntress Labs now report that Gootloader has returned in a brand new marketing campaign that when once more impersonates authorized paperwork.
“On this newest marketing campaign, we have noticed hundreds of distinctive key phrases unfold over 100 web sites,” reads a new weblog publish by the Gootloader researcher. “The last word objective stays the identical: persuade victims to obtain a malicious ZIP archive containing a JScript (.JS) file that establishes preliminary entry for follow-on exercise — often resulting in ransomware deployment.”
Supply: Huntress Labs
Nonetheless, the researchers say this new variant makes use of a couple of methods to evade automated evaluation instruments and safety researchers.
Huntress discovered that the JavaScript added to malicious web sites hides the true filenames through the use of a particular internet font that replaces letters with look-alike symbols.
Within the HTML supply, you see nonsense textual content, however when the web page is rendered, the font’s swapped glyph shapes show regular phrases, making it more durable for safety software program and researchers to search out key phrases like “bill” or “contract” within the supply code.
“Relatively than utilizing OpenType substitution options or character mapping tables, the loader swaps what every glyph truly shows. The font’s metadata seems fully professional—the character “O” maps to a glyph named “O”, the character “a” maps to a glyph named “a”, and so forth,” explains Huntress.
“Nonetheless, the precise vector paths that outline these glyphs have been swapped. When the browser requests the form for glyph “O”, the font supplies the vector coordinates that draw the letter “F” as a substitute. Equally, “a” attracts “l”, “9” attracts “o”, and particular Unicode characters like “±” draw “i”. The gibberish string Oa9Z±h• within the supply code renders as “Florida” on display.”
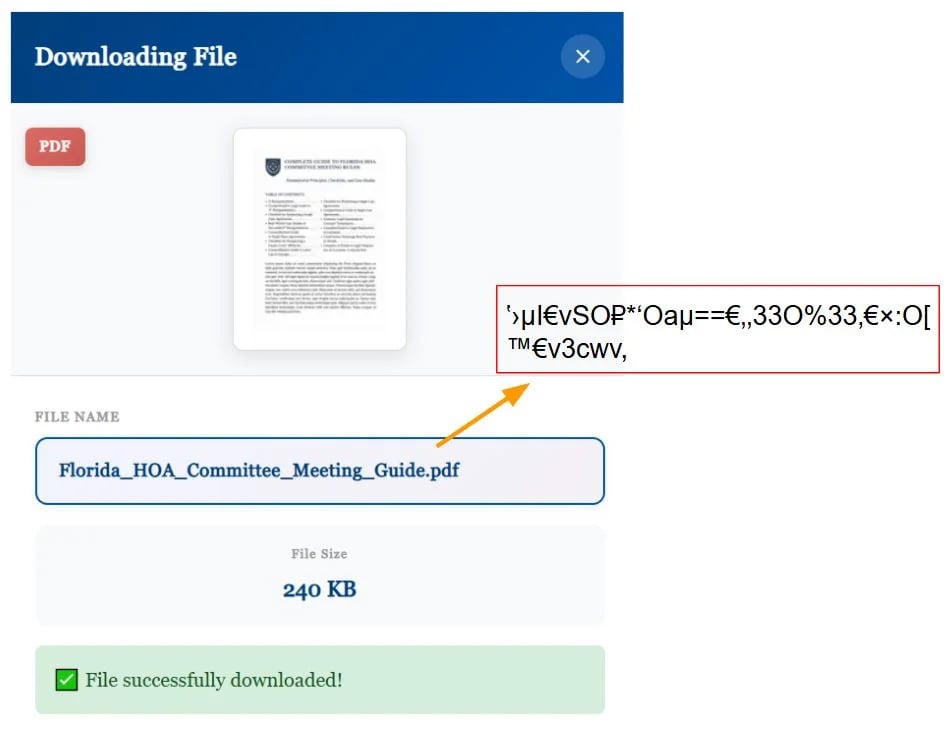
Supply: Huntress Labs
Researchers from the DFIR Report additionally found that Gootloader is utilizing malformed Zip archives to distribute Gootloader scripts from attacker-controlled web sites.
These archives are crafted in order that when the downloaded ZIP file is extracted with Home windows Explorer, the malicious JavaScript file, Review_Hearings_Manual_2025.js, is extracted.
Nonetheless, that very same archive, when extracted inside VirusTotal, Python’s zip utilities, or 7-Zip, will unpack a innocent textual content file named Review_Hearings_Manual_202.txt.
As you possibly can see within the picture beneath of 010 Editor, the archive accommodates each recordsdata however is malformed, inflicting it to be extracted in another way relying on the device used.
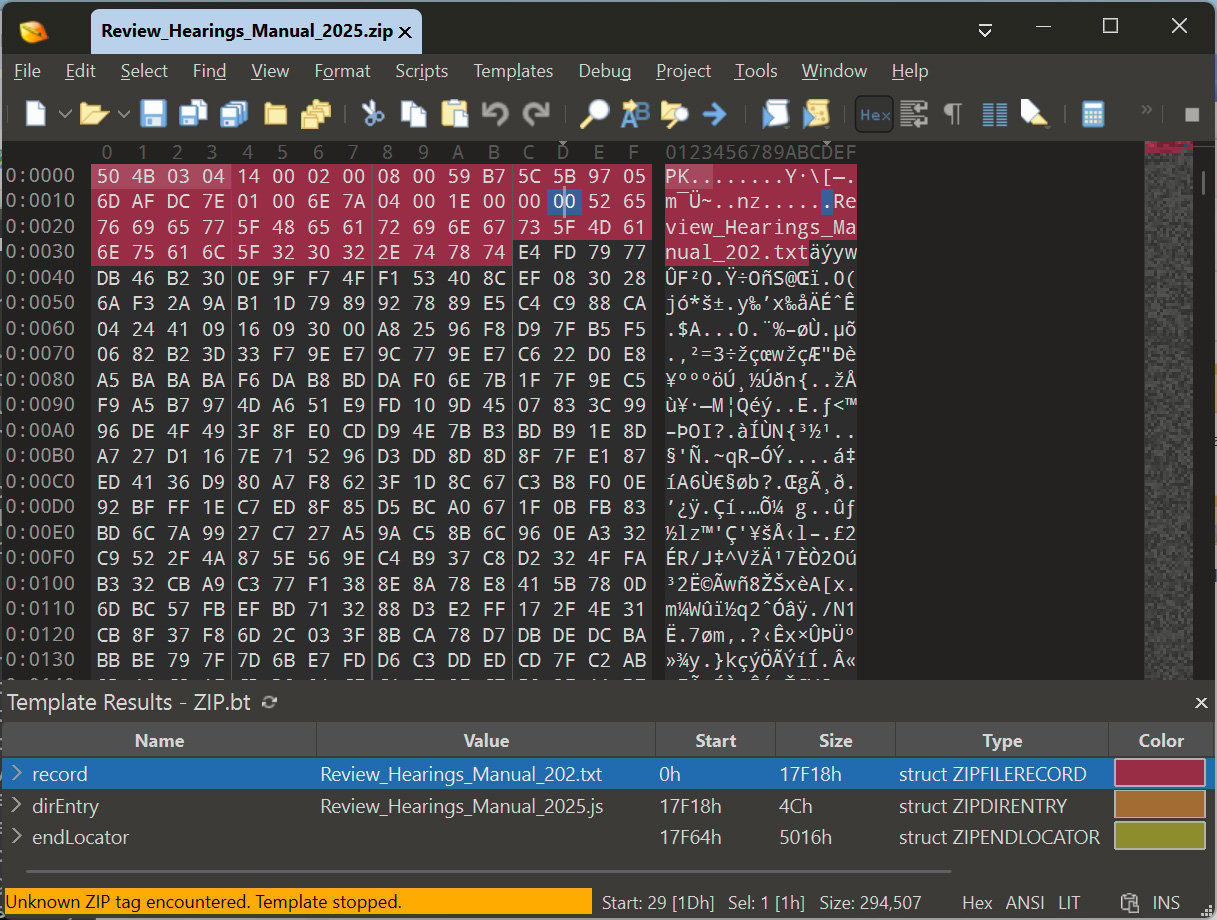
Supply: BleepingComputer
It is unclear whether or not this is identical concatenation trick described in 2024 or if they’re utilizing a brand new approach to get Home windows to extract the JS file.
Lastly, the marketing campaign is dropping the Supper SOCKS5 backdoor on units, which is used to realize distant entry to the community.
The Supper backdoor is malware that gives distant entry to contaminated units and is understood for use by a ransomware affiliate tracked as Vanilla Tempest.
This menace actor has a protracted historical past of conducting ransomware assaults and is believed to have been an affiliate of Inc, BlackCat, Quantum Locker, Zeppelin, and Rhysida.
Within the assaults noticed by Huntress, the menace actor moved quick as soon as a tool was contaminated, performing reconnaissance inside 20 minutes and in the end compromising the Area Controller inside 17 hours.
With Gootloader now again in operation, shoppers and company customers must be cautious about trying to find and downloading authorized agreements and templates from the net.
Except the web site is understood for providing these kinds of templates, it ought to be handled with suspicion and averted.
It is price range season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the 12 months forward. This report compiles their insights, permitting readers to benchmark methods, establish rising developments, and examine their priorities as they head into 2026.
Find out how prime leaders are turning funding into measurable impression.



