
Members of the North Korean hacker group Lazarus posing as recruiters are baiting Python builders with coding check undertaking for password administration merchandise that embrace malware.
The assaults are a part of the ‘VMConnect marketing campaign’ first detected in August 2023, the place the risk actors focused software program builders with malicious Python packages uploaded onto the PyPI repository.
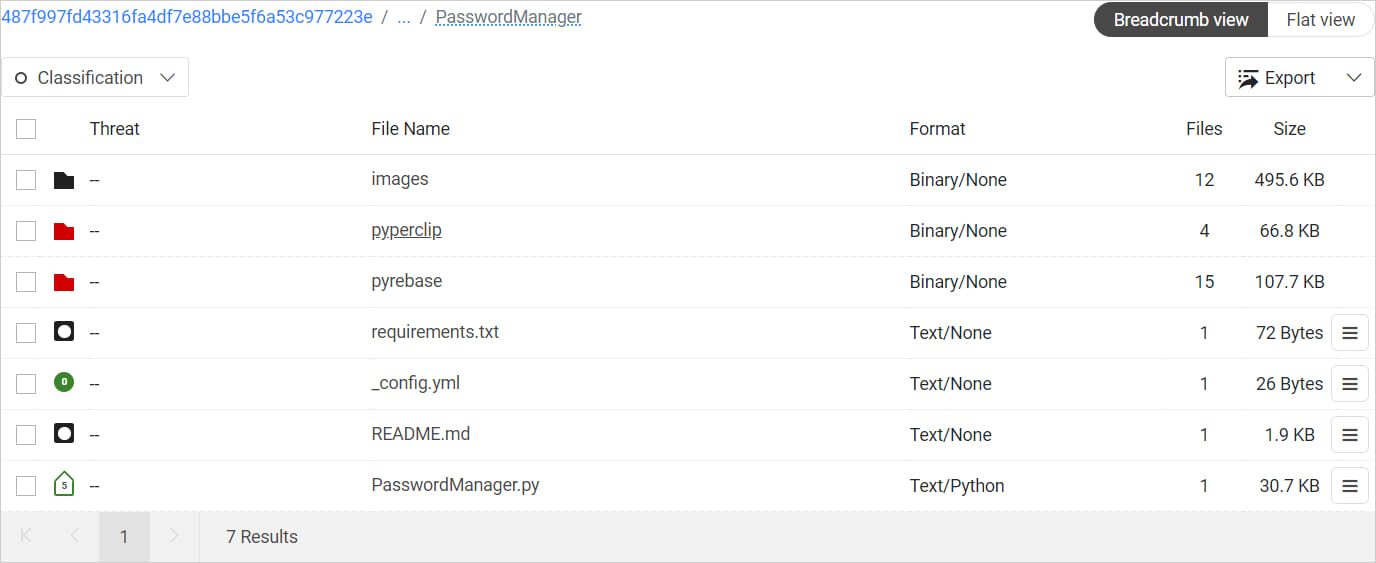
Based on a report from ReversingLabs, which has been monitoring the marketing campaign for over a 12 months, Lazarus hackers host the malicious coding initiatives on GitHub, the place victims discover README recordsdata with directions on find out how to full the check.
The instructions are supposed to present a way professionalism and legitimacy to the entire course of, in addition to a way of urgency.
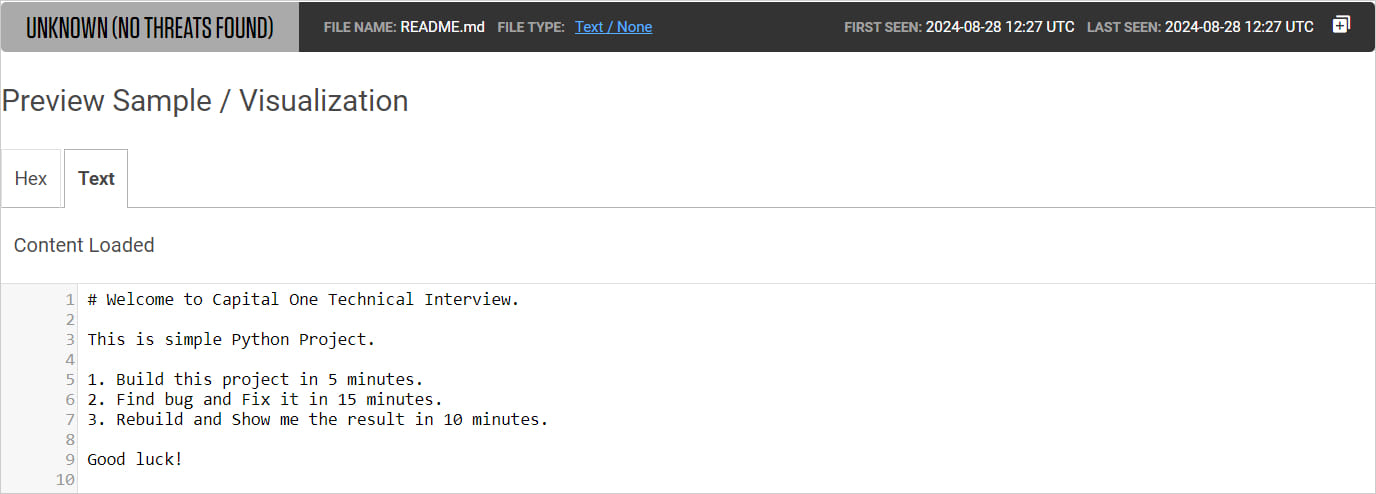
ReversingLabs discovered that the North Koreans impersonate massive U.S. banks like Capital One to draw job candidates, probably providing them an attractive employment package deal.
Additional proof retrieved from one of many victims means that Lazarus actively approaches their targets over LinkedIn, a documented tactic for the group.
Discover the bug
The hackers direct candidates to discover a bug in a password supervisor software, submit their repair, and share a screenshot as proof of their work.
Supply: ReversingLabs
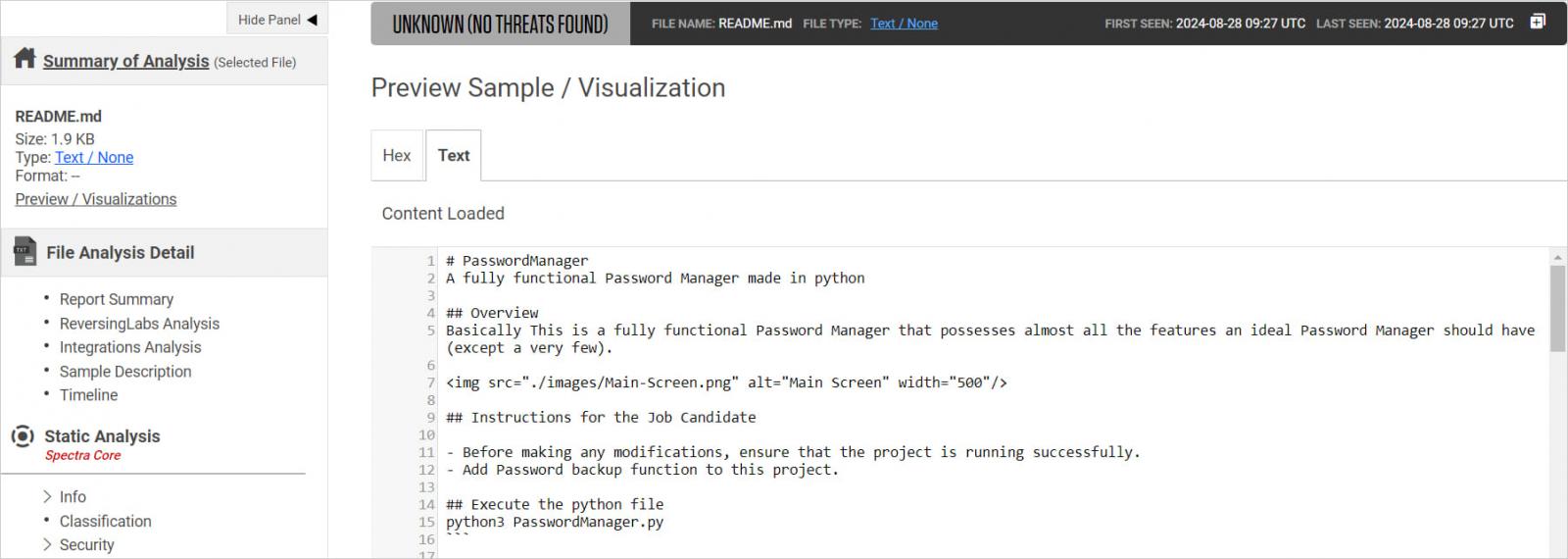
The README file for the undertaking instruct the sufferer first to execute the malicious password supervisor software (‘PasswordManager.py’) on their system after which begin in search of the errors and fixing them.
Supply: ReversingLabs
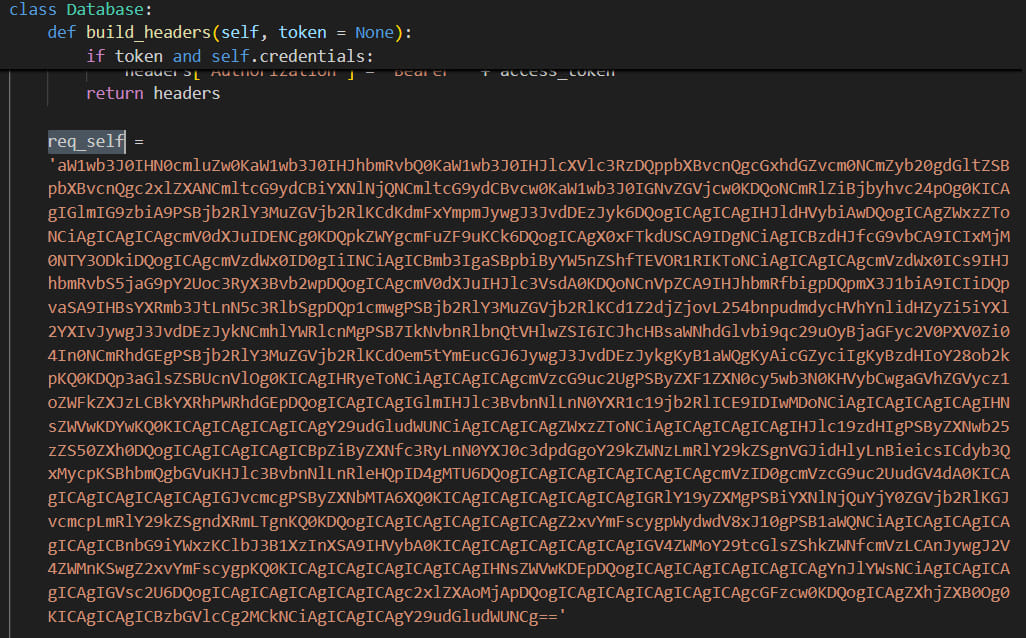
That file triggers the execution of a base64 obfuscated module hidden within the’_init_.py’ recordsdata of the ‘pyperclip’ and ‘pyrebase’ libraries.
The obfuscated string is a malware downloader that contacts a command and management (C2) server and awaits for instructions. Fetching and working further payloads is inside its capabilities.
Supply: ReversingLabs
To ensure that the candidates will not examine the undertaking recordsdata for malicious or obfuscated code, the README file require the duty to be accomplished rapidly: 5 minutes for constructing the undertaking, quarter-hour to implement the repair, and 10 minutes to ship again the ultimate consequence.
That is speculated to show the developer’s experience in working with Python initiatives and GitHub, however the objective is to make the sufferer skip any safety checks that will reveal the malicious code.
Supply: ReversingLabs
ReversingLabs has discovered proof that the marketing campaign was nonetheless energetic on July 31 and consider that it’s ongoing.
Software program builders receiving job software invitations from customers on LinkedIn or elsewhere must be cautious about the potential of deception and take into accounts that the profiles contacting them might be pretend.
Earlier than receiving the task, attempt to confirm the opposite particular person’s id and independently affirm with the corporate {that a} recruitment spherical is certainly underway.
Take the time to scan or fastidiously overview the given code and solely execute it in protected environments corresponding to digital machines or sandboxing purposes.

