
A risk actor has launched over 15 million e-mail addresses related to Trello accounts that have been collected utilizing an unsecured API in January.
Trello is a web based undertaking administration instrument owned by Atlassian. Companies generally use it to arrange knowledge and duties into boards, playing cards, and lists.
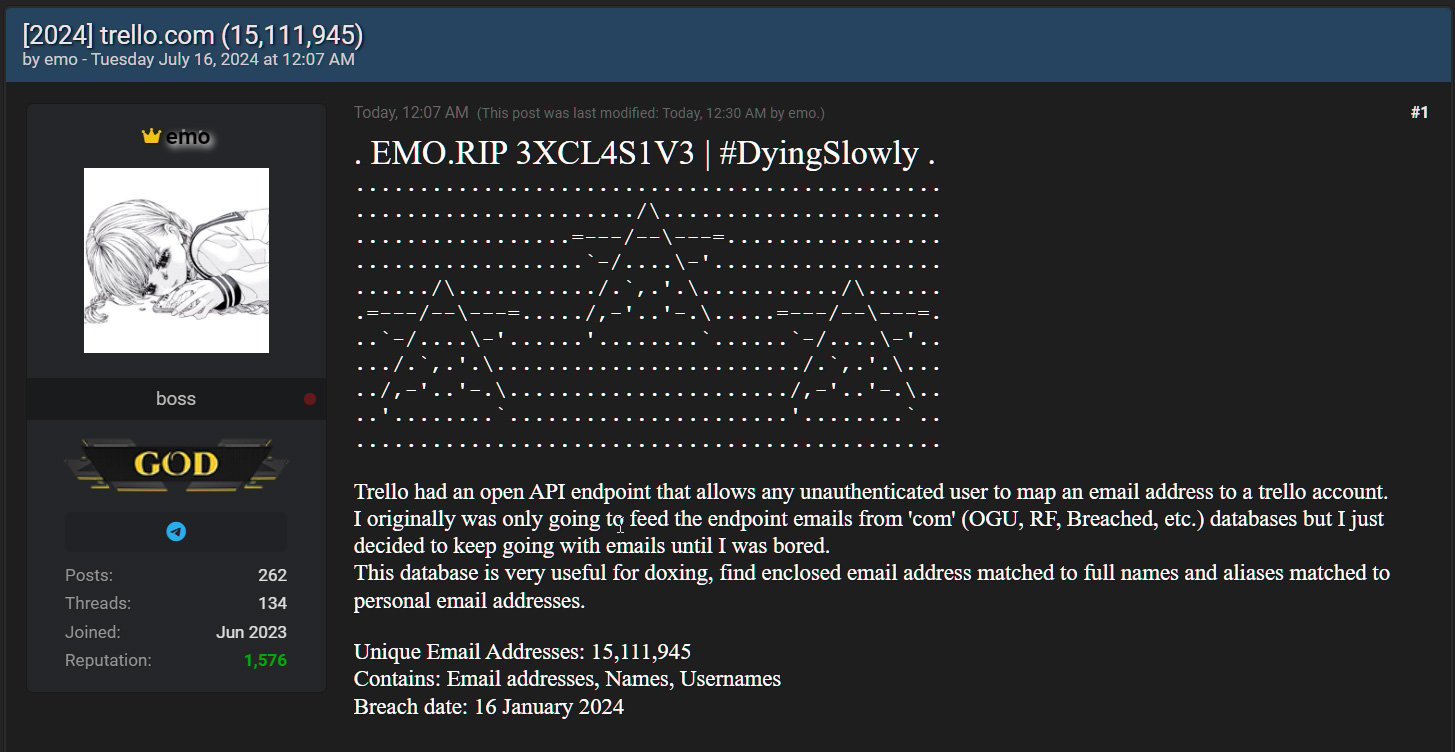
In January, BleepingComputer reported {that a} risk actor generally known as ’emo’ was promoting profiles for 15,115,516 Trello members on a well-liked hacking discussion board.
Whereas virtually all the knowledge in these profiles is public info, every profile additionally contained a private e-mail handle related to the account.
Whereas Atlassian, the proprietor of Trello, didn’t affirm on the time how the info was stolen, emo advised BleepingComputer it was collected utilizing an unsecured REST API that allowed builders to question for public details about a profile primarily based on customers’ Trello ID, username, or e-mail handle.
emo created an inventory of 500 million e-mail addresses and fed it into the API to find out in the event that they have been linked to a Trello account. The record was then mixed with the returned account info to create member profiles for over 15 million customers.
At present, emo shared the whole record of 15,115,516 profiles on the Breached hacking discussion board for eight website credit (price $2.32).
“Trello had an open API endpoint that enables any unauthenticated consumer to map an e-mail handle to a trello account,” emo defined within the discussion board publish.
“I initially was solely going to feed the endpoint emails from ‘com’ (OGU, RF, Breached, and many others.) databases however I simply determined to maintain going with emails till I used to be bored.”
The leaked knowledge contains e-mail addresses and public Trello account info, together with the consumer’s full title.
This info can be utilized in focused phishing assaults to steal extra delicate info, equivalent to passwords. emo additionally says the info can be utilized for doxxing, permitting risk actors to hyperlink e-mail addresses to individuals and their aliases.
Atlassian confirmed to BleepingComputer at present that the knowledge was collected by a Trello REST API that was secured in January.
“Enabled by the Trello REST API, Trello customers have been enabled to ask members or friends to their public boards by e-mail handle. Nevertheless, given the misuse of the API uncovered on this January 2024 investigation, we made a change to it in order that unauthenticated customers/providers can not request one other consumer’s public info by e-mail. Authenticated customers can nonetheless request info that’s publicly out there on one other consumer’s profile utilizing this API. This alteration strikes a steadiness between stopping misuse of the API whereas retaining the ‘invite to a public board by e-mail’ characteristic working for our customers. We’ll proceed to watch using the API and take any obligatory actions.”
❖ Atlassian
Unsecured APIs have turn out to be a well-liked goal for risk actors, who abuse them to mix private info, equivalent to e-mail addresses and cellphone numbers, with public profiles.
In 2021, risk actors abused an API to hyperlink cellphone numbers to Fb accounts, creating profiles for 533 million customers.
In 2022, Twitter suffered an identical breach when risk actors abused an unsecured API to hyperlink cellphone numbers and e-mail addresses to hundreds of thousands of customers.
As many individuals publish anonymously on social media, this knowledge allowed for the unmasking of those individuals, posing a big privateness threat.
Extra just lately, an unsecured Twilio API was used to verify the cellphone numbers of 33 million Authy multi-factor authentication app customers.
Many organizations try to safe APIs utilizing rate-limiting reasonably than by authentication through an API key.
Nevertheless, risk actors merely buy tons of of proxy servers and rotate the connections to always question the API, making the speed limiting ineffective.


