
EncryptHub, a infamous menace actor linked to breaches at 618 organizations, is believed to have reported two Home windows zero-day vulnerabilities to Microsoft, revealing a conflicted determine straddling the road between cybercrime and safety analysis.
The reported vulnerabilities are CVE-2025-24061 (Mark of the Net bypass) and CVE-2025-24071 (File Explorer spoofing), which Microsoft addressed through the March 2025 Patch Tuesday updates, acknowledging the reporter as ‘SkorikARI with SkorikARI .’
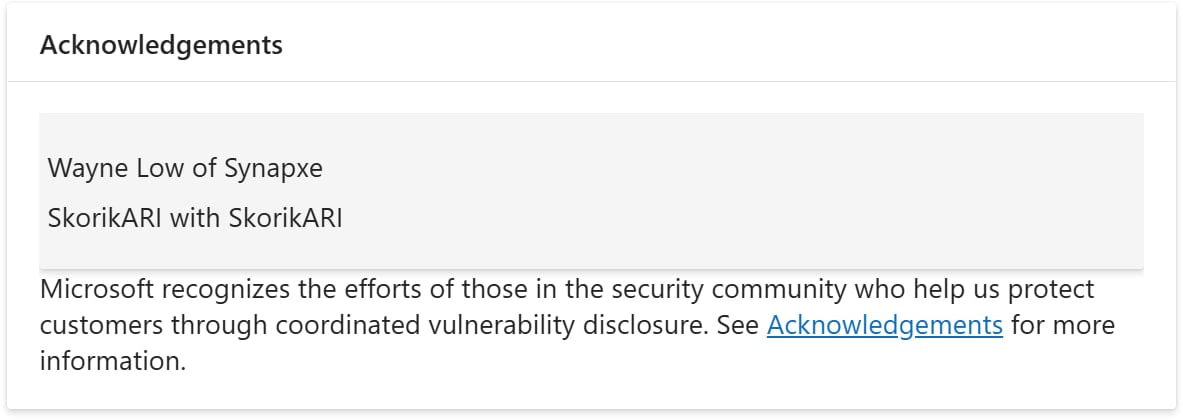
Supply: Microsoft
A new report by Outpost24 researchers has now linked the EncryptHub menace actor with SkorikARI after the menace actor allegedly contaminated himself and uncovered their credentials.
This publicity allowed the researchers to hyperlink the menace actor to numerous on-line accounts and expose the profile of an individual who vacillates between being a cybersecurity researcher and a cybercriminal.
One of many uncovered accounts is SkorikARI, which the hacker used to reveal the 2 talked about zero-day vulnerabilities to Microsoft, contributing to Home windows safety.
Hector Garcia, Safety Analyst at Outpost24, advised BleepingComputer that the hyperlink of SkorikARI to EncryptHub relies on a number of items of proof, making up for a high-confidence evaluation.
“The toughest proof was from the truth that the password recordsdata EncrypHub exfiltrated from his personal system had accounts linked to each EncryptHub, like credentials to EncryptRAT, which was nonetheless in growth, or his account on xss.is, and to SkorikARI, like accesses to freelance websites or his personal Gmail account,” defined Garcia.
“There was additionally a login to hxxps:// github[.]com/SkorikJR, which was talked about in July’s Fortinet Article about Fickle Stealer, bringing all of it collectively.”
“One other enormous affirmation of the hyperlink between the 2 had been the conversations with ChatGPT, the place exercise associated each to EncryptHub and to SkorikARI might be noticed.”
EncryptHub’s foray into zero-days just isn’t new, with the menace actor or one of many members making an attempt to promote zero-days to different cybercriminals on hacking boards.
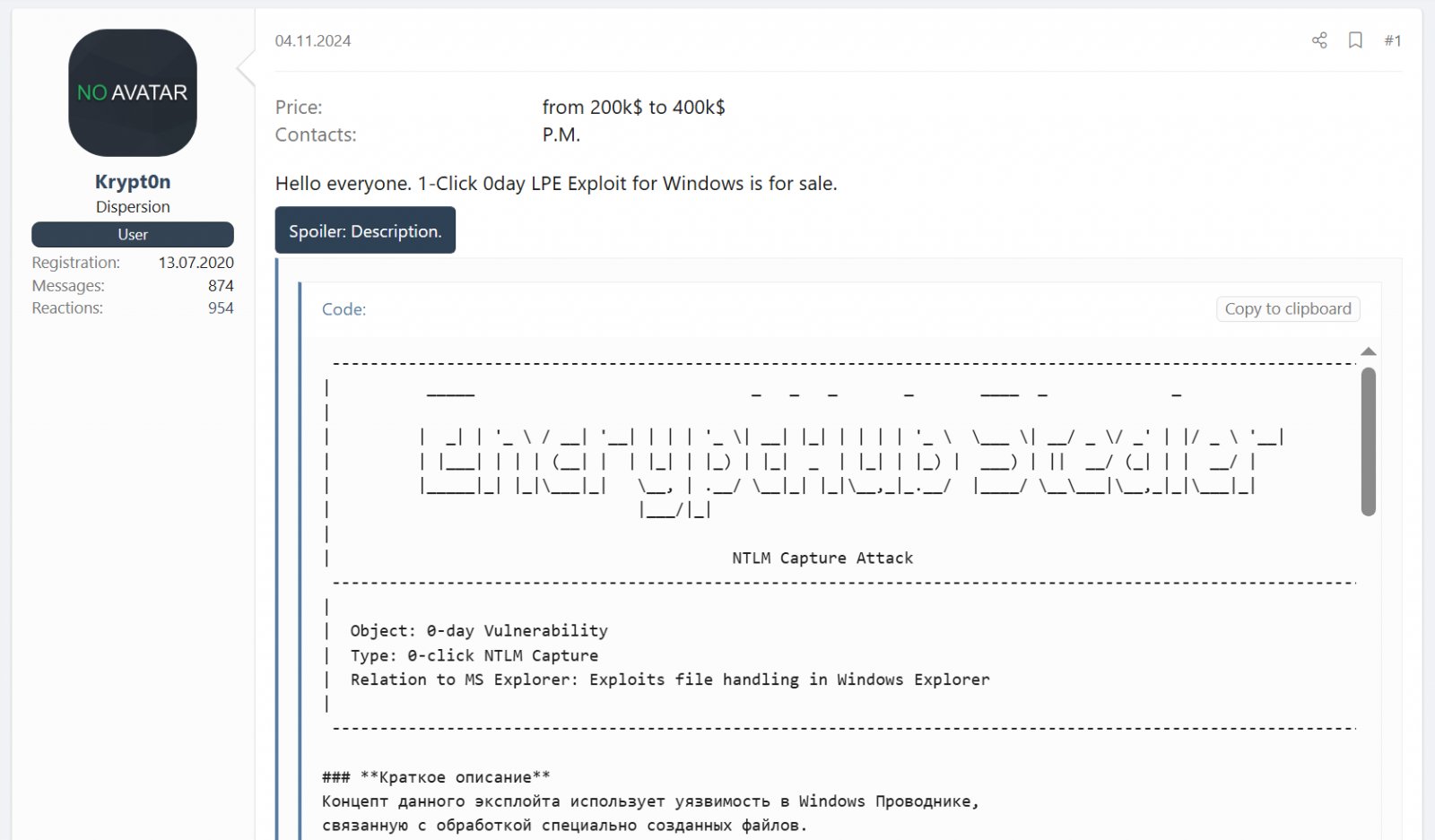
Supply: BleepingComputer
Outpost24 delved into EncryptHub’s journey, stating that the hacker repeatedly shifts between freelance growth work and cybercrime exercise.
Regardless of his obvious IT experience, the hacker reportedly fell sufferer to dangerous opsec practices that allowed his private data to be uncovered.
This consists of the hacker’s use of ChatGPT for creating malware and phishing websites, integrating third-party code, and researching vulnerabilities.
The menace actor additionally had a deeper, private engagement with OpenAI’s LLM chatbot, in a single case describing his accomplishments and asking the AI to categorize him as a cool hacker or malicious researcher.
Based mostly on the supplied inputs, ChatGPT assessed him as 40% black hat, 30% gray hat, 20% white hat, and 10% unsure, reflecting a morally and virtually conflicted particular person.
The identical battle is mirrored in his future planning on ChatGPT, the place the hacker asks for the chatbot’s assist in organizing an enormous however “innocent” marketing campaign impacting tens of hundreds of computer systems for publicity.

Supply: Outlook24
Who’s EncryptHub
EncryptHub is a menace actor that’s believed to be loosely affiliated with ransomware gangs, comparable to RansomHub and the BlackSuit operations.
Nevertheless, extra just lately, the menace actors have made a reputation for themselves with varied social engineering campaigns, phishing assaults, and making a customized PowerShell-based infostealer named Fickle Stealer.
The menace actor can be identified for conducting social engineering campaigns the place they create social media profiles and web sites for fictitious functions.
In a single instance, researchers discovered that the menace actor created an X account and web site for a mission administration utility referred to as GartoriSpace.
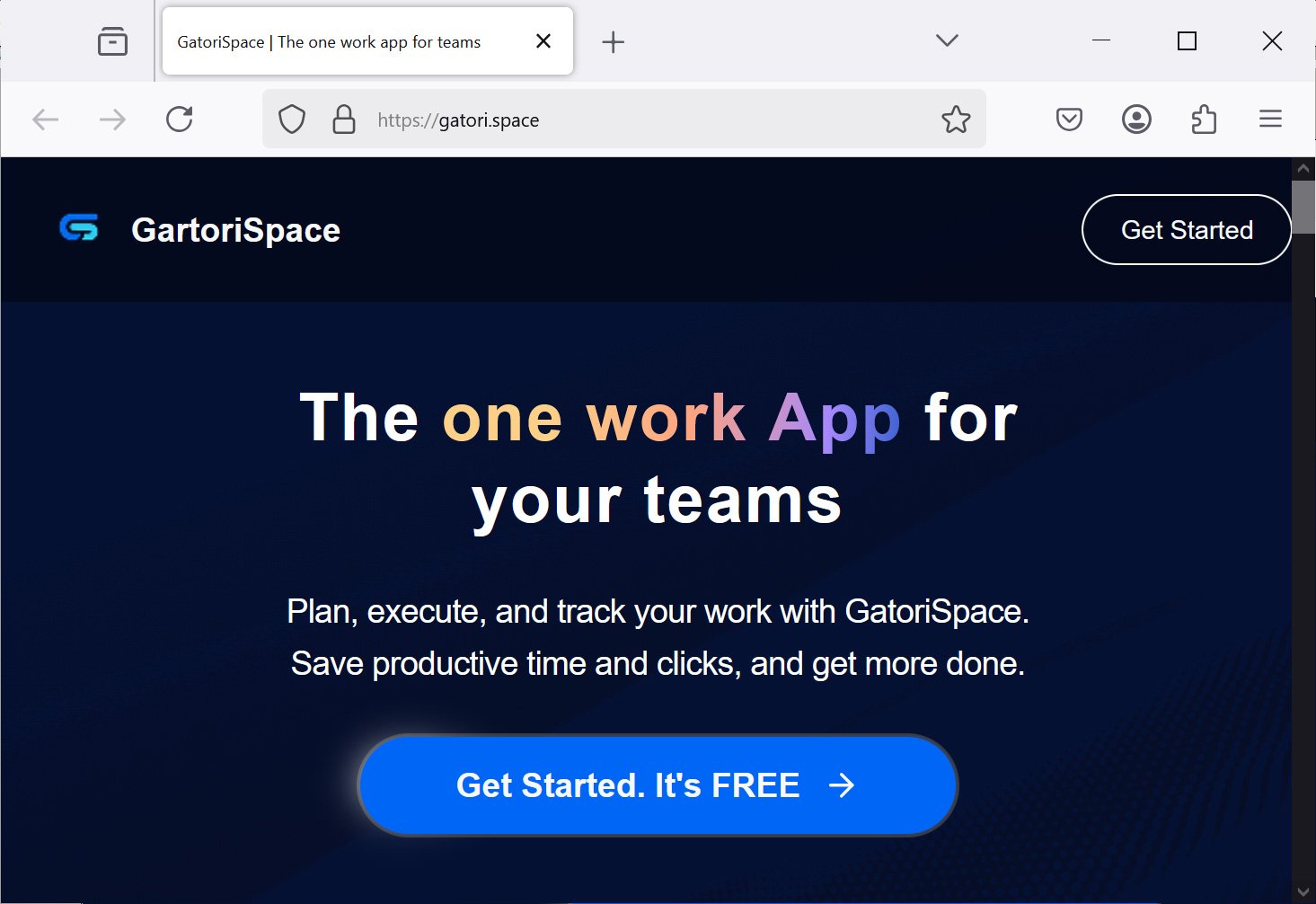
Supply: BleepingComputer
This website was promoted by means of non-public messages on social media platforms that would supply a code required to obtain the software program. When downloading the software program, Home windows gadgets would obtain a PPKG file [VirusTotal] that put in Fickle Stealer, and Mac gadgets would obtain the AMOS information-stealer [VirusTotal].
EncryptHub has additionally been linked to Home windows zero-day assaults exploiting a Microsoft Administration Console vulnerability tracked as CVE-2025-26633. The flaw was fastened in March however was attributed to Pattern Micro quite than the menace actor.
Total, the menace actors’ campaigns seem like working for them as a report by Prodaft says the menace actors have compromised over 600 organizations.


