
The Clop ransomware gang has confirmed to BleepingComputer that they’re behind the current Cleo data-theft assaults, using zero-day exploits to breach company networks and steal information.
Cleo is the developer of the managed file switch platforms Cleo Concord, VLTrader, and LexiCom, which corporations use to securely trade information between their enterprise companions and clients.
In October, Cleo fastened a vulnerability tracked as CVE-2024-50623 that allowed unrestricted file uploads and downloads, resulting in distant code execution.
Nevertheless, cybersecurity agency Huntress found final week that the unique patch was incomplete and risk actors had been actively exploiting a bypass to conduct information theft assaults.
Whereas exploiting this vulnerability, the risk actors had been importing a JAVA backdoor that allowed the attackers to steal information, execute instructions, and achieve additional entry to the compromised community.
On Friday, CISA confirmed that the important CVE-2024-50623 safety vulnerability in Cleo Concord, VLTrader, and LexiCom file switch software program has been exploited in ransomware assaults. Nevertheless, Cleo by no means publicly disclosed that the unique flaw they tried to repair in October was exploited.
Clop claims accountability for Cleo information theft assaults
It was beforehand thought that the Cleo assaults had been performed by a brand new ransomware gang named Termite. Nevertheless, the Cleo information theft assaults tracked extra intently to earlier assaults performed by the Clop ransomware gang.
After contacting Clop on Tuesday, the ransomware gang confirmed to BleepingComputer that they’re behind the current exploitation of the Cleo vulnerability detected by Huntress in addition to the exploitation of the unique CVE-2024-50623 flaw fastened in October.
“As for CLEO, it was our challenge (together with the earlier cleo) – which was efficiently accomplished.
All the data that we retailer, when working with it, we observe all safety measures. If the information is authorities providers, establishments, medication, then we’ll instantly delete this information with out hesitation (let me remind you in regards to the final time when it was with moveit – all authorities information, medication, clinics, information of scientific analysis on the state degree had been deleted), we adjust to our laws.
with love © CL0P^_”
❖ Clop advised BleepingComputer
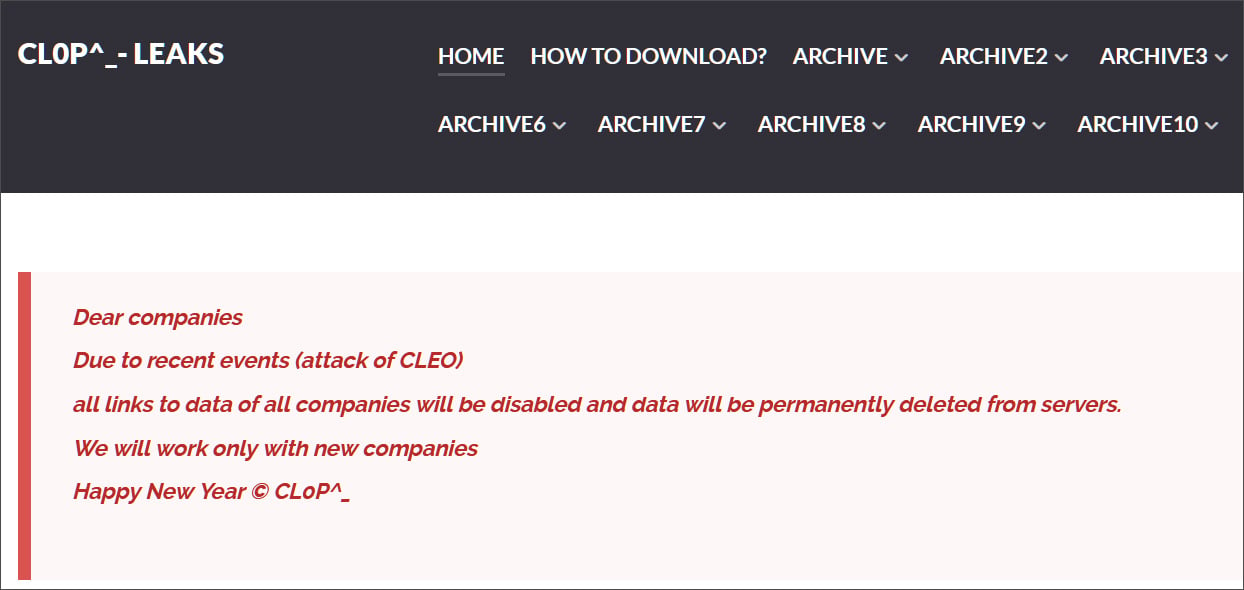
The extortion gang has now introduced that they’re deleting information related to previous assaults from their information leak server and can solely work with new corporations breached within the Cleo assaults.
“Pricey corporations, As a consequence of current occasions (assault of CLEO) all hyperlinks to information of all corporations will likely be disabled and information will likely be completely deleted from servers. We are going to work solely with new corporations,” reads a brand new message on the gang’s CL0P^_- LEAKS extortion web site.
“Blissful New Yr © CL0P^_ the entire victims from their information leak web site.”
Supply: BleepingComputer
BleepingComputer requested Clop when the assaults started, what number of corporations had been impacted, and if Clop was affiliated with the Termite ransomware gang, however didn’t obtain a response to those questions.
BleepingComputer additionally contacted Cleo on Friday to verify if Clop was behind the exploitation of the vulnerabilities however didn’t obtain a response.
Specializing in exploit file switch platforms
The Clop ransomware gang, aka TA505 and Cl0p, launched in March 2019, when it first started focusing on the enterprise utilizing a variant of the CryptoMix ransomware.
Like different ransomware gangs, Clop breached company networks and slowly unfold laterally by its techniques whereas stealing information and paperwork. Once they have harvested every part of worth, they deployed ransomware on the community to encrypt its units.
Nevertheless, since 2020, the ransomware gang has specialised in focusing on beforehand unknown vulnerabilities in safe file switch platforms for information theft assaults.
In December 2020, Clop exploited a zero-day within the Accellion FTA safe file switch platform, which impacted almost 100 organizations.
Then in 2021, the ransomware gang exploited a zero-day in SolarWinds Serv-U FTP software program to steal information and breach networks.
In 2023, Clop exploited a zero-day within the GoAnywhere MFT platform, permitting the ransomware gang to steal information from over 100 corporations once more.
Nevertheless, their most important assault of this sort was utilizing a zero-day within the MOVEit Switch platform that allowed them to steal information from 2,773 organizations, based on a report by Emsisoft.
Presently, it isn’t clear what number of corporations have been impacted by the Cleo information theft assaults, and BleepingComputer doesn’t know of any corporations who’ve confirmed being breached by the platform.
The U.S. State Division’s Rewards for Justice program at present has a $10 million bounty for info linking the Clop ransomware assaults to a overseas authorities.

