As cyber threats intensify and compliance expectations tighten, safety leaders more and more acknowledge that perimeter defenses alone can’t preserve tempo. Organizations are actually contending with 1000’s of assault makes an attempt every week and a every day flood of alerts that far exceed human capability to research.
Menace actors are exploiting AI-driven methods and fragmented visibility throughout networks, endpoints, and cloud environments, slipping by the gaps between edge defenses and SOC operations. It’s no shock {that a} majority of analysts imagine compromises might already be underway with out detection.
To counter this actuality, forward-leaning enterprises are transferring towards built-in safety fashions that join telemetry, context, and menace analytics from the perimeter all the way in which into the SOC.
The Rising Log Quantity Problem
Community environments generate huge volumes of safety knowledge every day. Usually, 25% of all community logs consumed are from firewalls, creating an awesome knowledge administration problem. Conventional approaches wrestle with:
- Knowledge Overload and Noise — Safety groups face overwhelming volumes of log knowledge from numerous sources, making it tough to prioritize and determine important alerts. An estimated 41% of alerts are ignored because of analyst bandwidth constraints.
- Correlation Complexity — Remoted firewall logs present restricted visibility into assault patterns that span a number of community segments and timeframes. Trendy threats make use of lateral motion methods that require cross-device correlation to detect successfully. A major impediment for SOC groups is the dearth of contextual info round safety occasions.
- Challenges With Knowledge Administration and Pipeline — Knowledge is the brand new gold, however how do you collect the information effectively and in a scalable style. Firewall logs are an indispensable element of contemporary knowledge administration pipeline. This requires that we help numerous business requirements for Firewall logs so it may be transformed into appropriate codecs for evaluation, whereas being simply consumed by Splunk Knowledge Administration Pipeline Builders; Edge Processor and Ingest Processor.
- Knowledge Retention and Compliance Pressures — Regulatory frameworks require complete logging and monitoring of all entry to system elements and cardholder knowledge. Organizations should keep detailed audit trails whereas making certain that delicate info stays protected all through the retention lifecycle.
The problem extends past easy storage. Organizations want clever knowledge administration that may robotically archive, index, and retrieve historic safety occasions for forensic evaluation and compliance reporting.
The AI Period: New Threats Demand New Approaches
The emergence of AI-powered assaults has essentially modified the menace panorama. Conventional signature-based detection strategies can not determine beforehand unknown assault vectors or adaptive malware that evolves in real-time. Organizations want behavioral analytics and machine studying capabilities to detect anomalous patterns that point out refined threats.
Flexibility in knowledge dealing with turns into important when coping with numerous log codecs, various occasion sorts, and the necessity to correlate firewall knowledge with endpoint, cloud, and utility safety occasions. Static logging configurations can not adapt to evolving menace patterns or altering compliance necessities.
Cisco Firewalls Meet Splunk Intelligence
Cisco Firewall Administration Middle (FMC) and Safety Cloud Management present in-built integration with Splunk for Firewall in upcoming launch.
- In constructed Guided Splunk integration workflow
- Splunk Log forwarding profile offers flexibility to decide on occasion sorts and gadgets
- Assist for UDP, TCP, and TLS protocols for safe transmission
- Different to eStreamer for sending occasions from FMC to Splunk
- Three versatile system choice strategies: Administration interfaces, Safety Zones, or Guide choice
- Area-specific configuration help for multi-tenant environments
- Occasion Sorts Supported are Connection, Intrusion, Malware, File, Consumer exercise, Correlation, Discovery and Intrusion packet occasions from FMC.


Shifting Past Legacy Logging
The combination permits organizations to transition from legacy eStreamer implementations to extra versatile syslog-based knowledge assortment. Whereas eStreamer offered wealthy knowledge, the brand new Splunk integration workflow moreover presents:
- Simplified configuration and integration workflow
- Diminished infrastructure complexity
- Higher scalability for high-volume environments
- Native integration with Cisco Safety Cloud App
Advantages Submit-Integration: Reworking Safety Operations
Actual-Time Dashboards and Visualization
Integration transforms uncooked firewall knowledge into actionable safety intelligence by customizable dashboards that present real-time visibility into community threats, person conduct, and compliance standing. Safety groups achieve fast perception into connection patterns, intrusion makes an attempt, malware detection, and coverage violations.
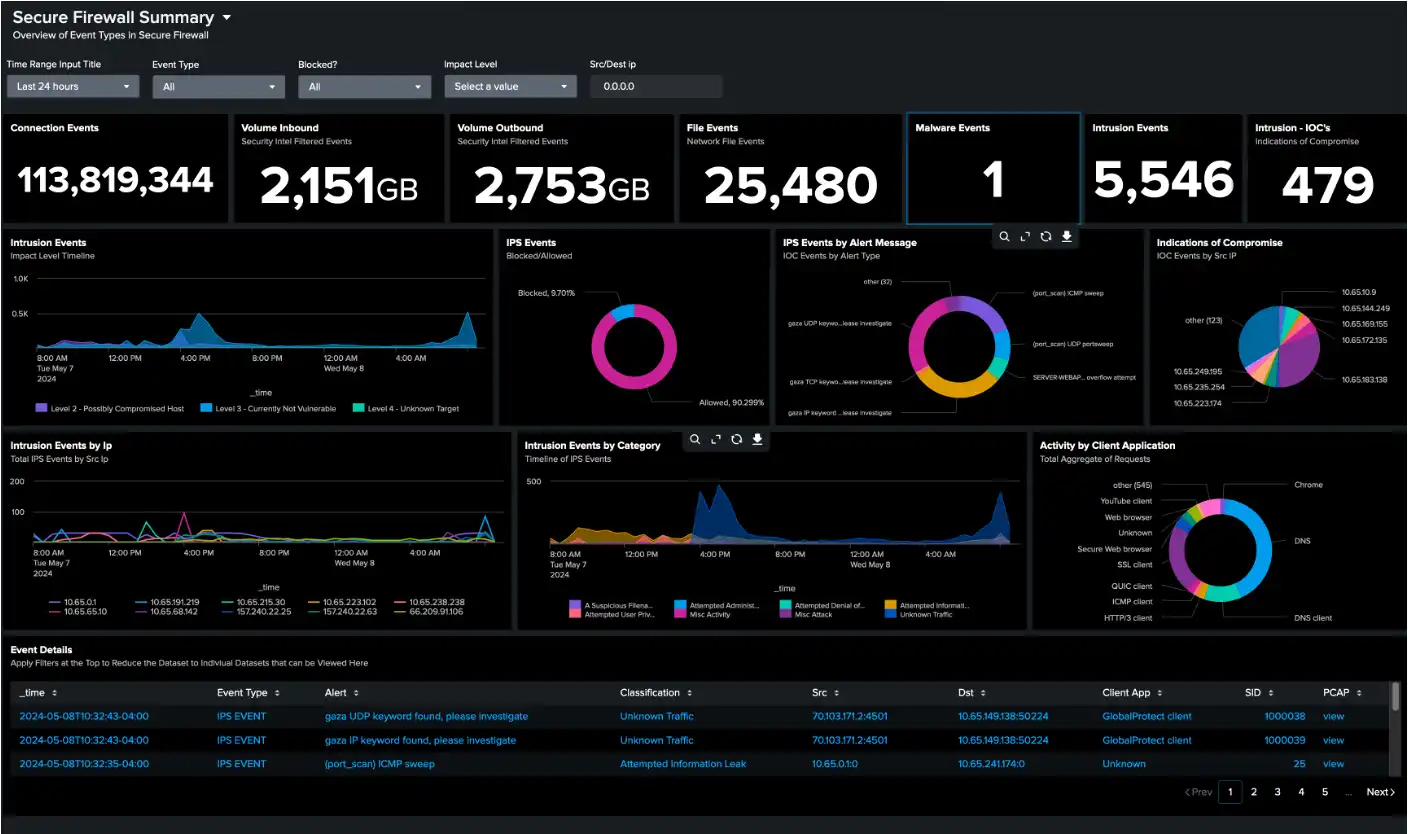

Interactive visualizations allow drill-down evaluation from high-level metrics to particular occasion particulars. Groups can observe menace traits over time, determine assault sources, and monitor the effectiveness of safety controls by dynamic reporting interfaces.
Superior Menace Detection with Splunk Enterprise Safety 8.2
The Splunk Menace Analysis Group (STRT) together with Cisco Talos has developed focused menace detections particularly for Cisco Safe Firewall integration. This collaboration analyzed over 650,000 occasions throughout 4 completely different occasion sorts in simply 60 days to create production-ready detections that present fast SOC worth.
Key Detection Examples:
- Cisco Safe Firewall — BITS Community Exercise
This detection identifies probably suspicious use of the Home windows BITS service by leveraging Cisco Safe Firewall’s built-in utility detectors. BITS is usually utilized by adversaries to ascertain command-and-control channels whereas showing as reputable Home windows replace visitors. - Cisco Safe Firewall — Binary File Sort Obtain
This analytic detects file downloads involving executable, archive, or scripting-related file sorts generally utilized in malware supply, together with PE executables, shell scripts, autorun recordsdata, and installers. - Cisco Safe Firewall — Excessive Quantity of Intrusion Occasions Per Host
This detection identifies programs triggering an unusually excessive variety of intrusion alerts inside a 30-minute window, which can point out an energetic assault or compromise. The detection aggregates occasions to cut back false positives whereas highlighting programs below energetic menace.
The detections are organized into the Cisco Safe Firewall Menace Protection Analytics analytic story, out there by Enterprise Safety Content material Replace (ESCU) 5.4.0 launch, with every detection mapped to the MITRE ATT&CK framework for enhanced menace context.
Extra particulars might be discovered on the Splunk weblog.
Compliance With Splunk: How It Exhibits Up for Firewall Clients
Splunk presents highly effective capabilities for performing compliance checks by automating the monitoring, evaluation, and reporting of compliance controls throughout IT environments.
It helps pre-built dashboards and visualizations tailor-made for safety and compliance monitoring primarily based on Firewall Occasions, akin to PCI Compliance Posture and Audit Dashboards. Utilizing Splunk Compliance Necessities app, you’ll be able to regularly monitor the compliance posture throughout numerous management frameworks like CMMC, FISMA, RMF, DFARS, and even OMB M-21-31.
Splunk will help companies adjust to the Federal Data Safety Modernization Act (FISMA), by aligning with safety controls as articulated in NIST Particular Publication 800-53.
Name to Motion
Leverage the Cisco Firewall Promotional Splunk Provide
Beginning August 2025, ingestion of logs from Cisco Safe Firewalls into Splunk will likely be FREE as much as 5GB per day. This revolutionary supply requires a Cisco Firewall Menace Protection subscription and Splunk license, eradicating price limitations to complete safety monitoring.
The free ingestion program permits organizations to expertise the total advantages of built-in menace detection and compliance reporting. This initiative demonstrates the strategic partnership between Cisco and Splunk in delivering accessible, highly effective safety options. Extra particulars on eligibility standards on the Splunk web site.
Logging Finest Practices
When implementing Cisco firewall integration with Splunk, organizations ought to comply with these established greatest practices:
Logging Configuration
- Configure acceptable log ranges to stability visibility with quantity administration
- Implement log rotation and retention insurance policies aligned with compliance necessities
- Use TLS encryption for safe log transmission between firewalls and Splunk
- Arrange correct filtering to cut back noise whereas sustaining important safety visibility
Knowledge Administration
- Set up correct indexing methods to optimize search efficiency
- Configure knowledge retention insurance policies primarily based on regulatory and enterprise necessities
- Implement monitoring for knowledge pipeline well being and integrity
- Plan for scalable infrastructure to accommodate rising log volumes
Extra particulars might be discovered within the Safe Firewall documentation.
Find out how to get began
- Obtain the Cisco Safety Cloud App from Splunkbase
- Configure the mixing workflow out there within the upcoming launch of FMC 10.0 and Safety Cloud Management
- Arrange your first knowledge sources utilizing the guided configuration wizard
- Reap the benefits of the free 5GB every day ingestion to expertise unified safety visibility
The way forward for cybersecurity lies in clever integration that transforms remoted safety instruments into complete menace detection and response platforms. Organizations that embrace this evolution place themselves to fulfill each present and future safety challenges successfully, making certain enterprise resilience in an more and more advanced menace panorama.
We’d love to listen to what you assume! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media

