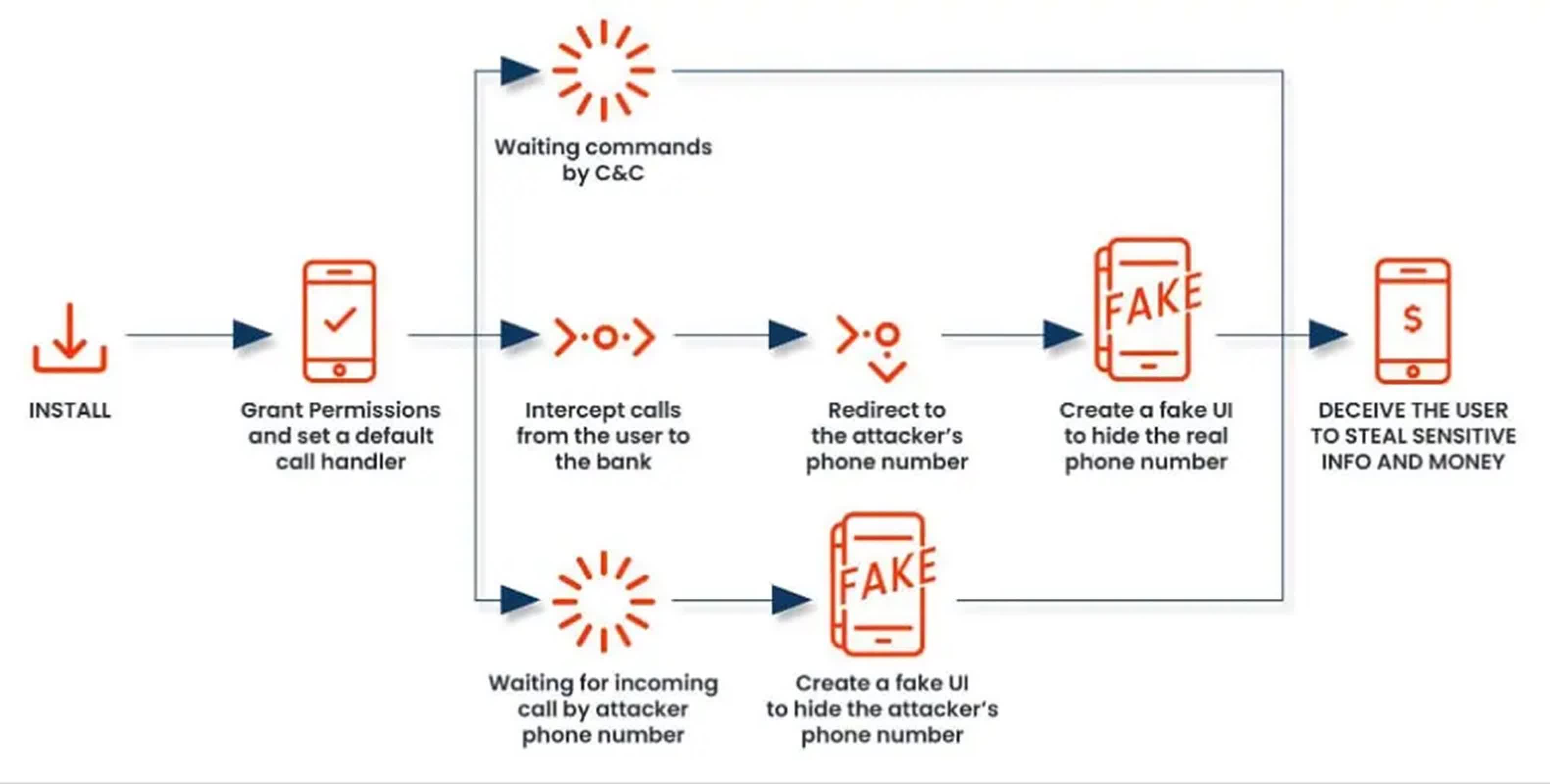
Backside line: Essentially the most alarming side of FakeCall is its skill to simulate incoming calls from financial institution workers. This characteristic is designed to reassure victims that nothing is amiss and to trick them into divulging account credentials by social engineering techniques.
First recognized in 2022, FakeCall is a malicious piece of software program that was developed to hijack financial institution accounts. It does this by intercepting calls made to monetary establishments after which redirecting them to cybercriminals who impersonate financial institution representatives to extract delicate data and achieve unauthorized entry to victims’ funds – a con known as voice phishing, or “vishing” for brief. Within the years since, it has undergone vital evolution and reemerged with alarming new capabilities, presenting a good higher hazard to Android customers around the globe.
A complete of 13 new variants of FakeCall have been found by researchers at cell safety agency Zimperium. They showcase a spread of latest and enhanced capabilities that point out a considerable funding by the attackers.
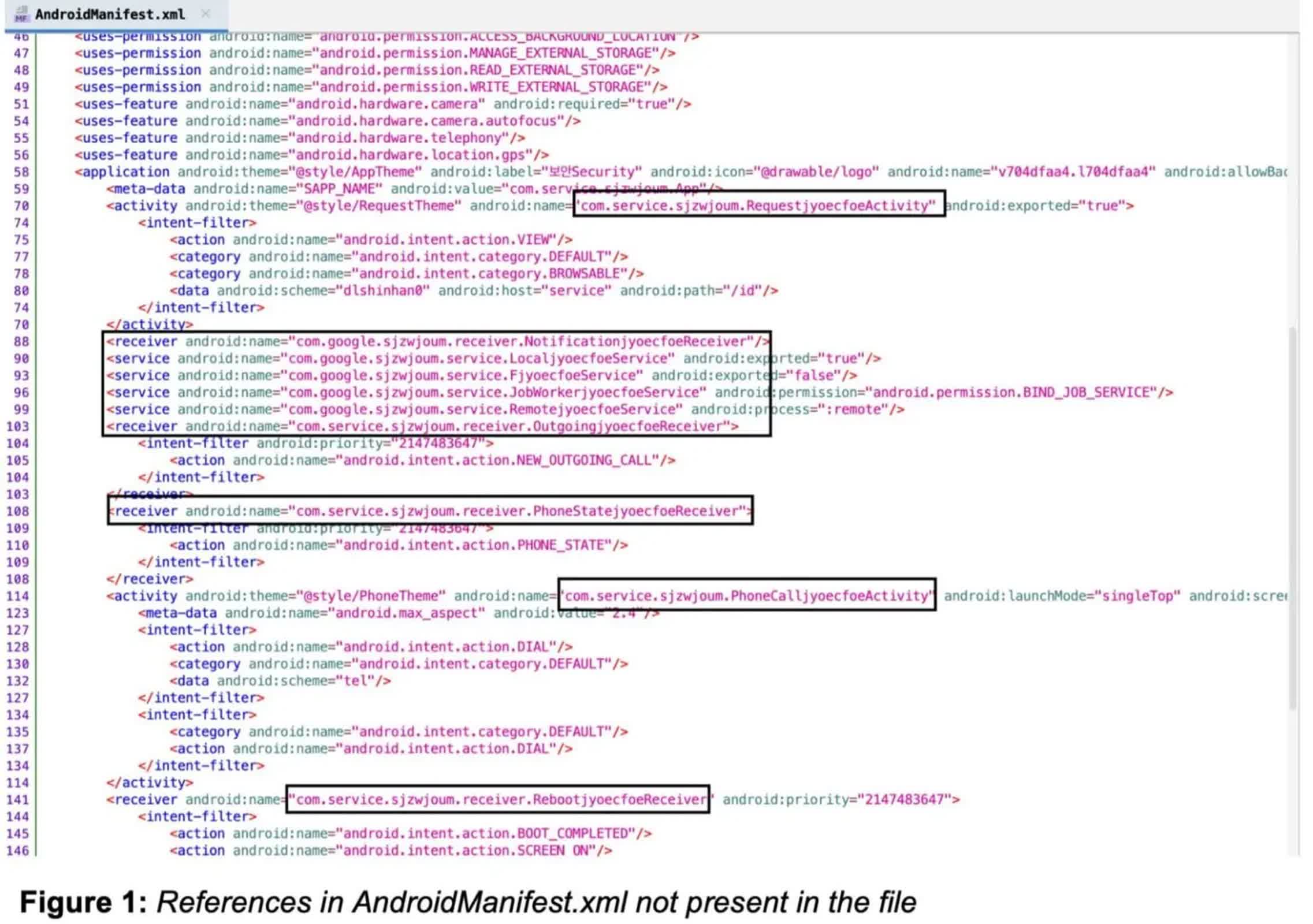
Probably the most vital developments is the elevated degree of obfuscation employed by the malware. The brand new variants make the most of a dynamically decrypted and loaded .dex file to hide their malicious code, making detection and evaluation tougher.
FakeCall’s major methodology of an infection is much like the sooner variations. The malware sometimes enters a sufferer’s gadget by a phishing assault, tricking customers into downloading an APK file that acts as a dropper. As soon as put in, this dropper deploys the malicious payload, establishing communication with a Command and Management (C2) server.
The malware’s core performance revolves round its skill to intercept and manipulate telephone calls. When put in, FakeCall prompts the person to set it because the gadget’s default name handler. This seemingly innocuous request grants the malware intensive management over all incoming and outgoing calls.
FakeCall’s subtle name interception system permits it to watch outgoing calls and transmit this data to its C2 server. When a sufferer makes an attempt to contact their financial institution, the malware can redirect the decision to a quantity managed by the attackers. To keep up the deception, FakeCall shows a convincing pretend person interface that mimics the respectable Android name interface, full with the true financial institution’s telephone quantity.
The newest variants of FakeCall introduce a number of new elements, a few of which seem like nonetheless in growth. A Bluetooth Receiver screens Bluetooth standing and adjustments, although its precise goal stays unclear. Equally, a Display Receiver screens the display’s state with none obvious malicious exercise within the supply code.
A brand new Accessibility Service, inherited from the Android Accessibility Service, grants the malware vital management over the person interface and the power to seize data displayed on the display; this demonstrates the malware’s elevated sophistication. Primarily based on evaluation of earlier variations, it may probably monitor dialer exercise, routinely grant permissions to the malware, and even enable distant attackers to take full management of the sufferer’s gadget UI.
Moreover, a Telephone Listener Service acts as a bridge between the malware and its command and management server, enabling attackers to situation instructions and execute actions on the contaminated gadget.