9to5Mac Safety Chew is completely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Technology EDR, AI-powered Zero Belief, and unique Privilege Administration with essentially the most highly effective and fashionable Apple MDM available on the market. The result’s a completely automated Apple Unified Platform presently trusted by over 45,000 organizations to make thousands and thousands of Apple gadgets work-ready with no effort and at an inexpensive value. Request your EXTENDED TRIAL at present and perceive why Mosyle is every part you must work with Apple.
Final week, Apple confirmed that customers on macOS Sequoia will now not be capable to Management-click to override Gatekeeper to open software program that isn’t signed or notarized by the corporate. This was a slight change with what I imagine may have a big influence. It additionally provides us a glimpse into what may occur behind the scenes at Apple as Mac malware will get extra intelligent and the quantity of it attain all-time highs.

I’ve at all times been baffled by how simply any non-sophisticated Jonny Appleseed person may bypass Mac’s two greatest security measures (Gatekeeper and XProtect) in simply two clicks.
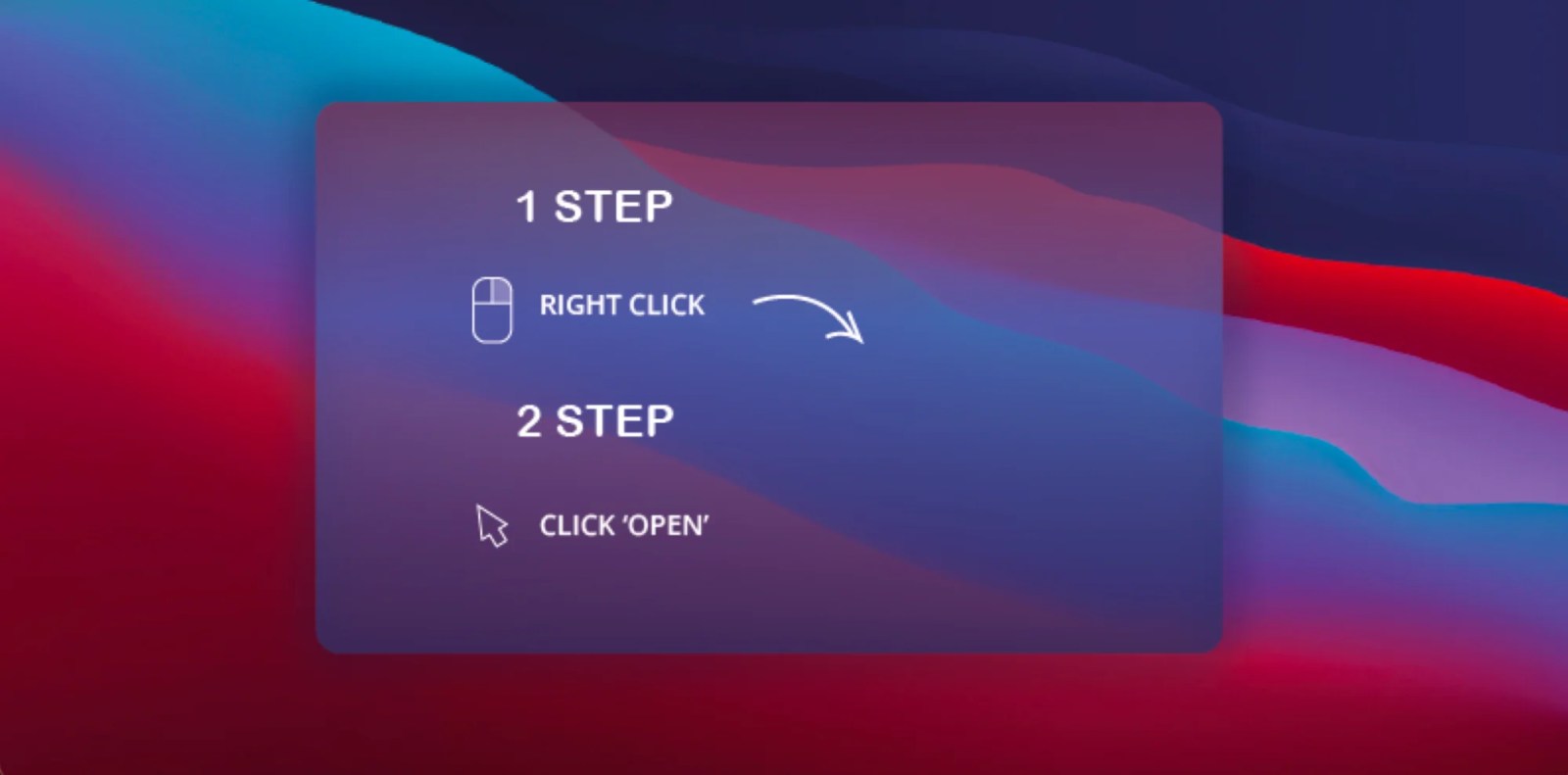
This sometimes occurs when a person makes an attempt to obtain unsigned software program, like a pirated software. Once they double-click to open it, macOS will current an error message stating, “[application.pkg] can’t be open as a result of it’s from an unidentified developer.” From right here, the person may let loose a fast sigh and Google the issue solely to seek out they only need to right-click the bundle and hit “Open.”
I perceive it’s a little bit of a catch-22 to say that “non-sophisticated” customers would know how one can bypass macOS Gatekeeper and the XProtect suite, not to mention discover and obtain pirated software program. Nevertheless, what in the event that they thought they have been putting in a official app, and that’s the way it instructed them to open it?
Malware authors are extra intelligent than ever. One of many newest traits is cloning actual purposes, usually productiveness apps like Notion or Slack, and injecting malware someplace within the code. Authors then create set up screens just like the one under, instructing the person to right-click and open the malware to get round Gatekeeper. The loopy half is that generally customers will go on to make use of these purposes for fairly a while and by no means know their system has been contaminated. Persistence is vital for cybercriminals.

Picture of Shlayer malware from Jamf.
Now in macOS Sequoia, customers might want to independently evaluate the app’s safety particulars in System Settings > Privateness & Safety earlier than it’s allowed to run. It’s nice to lastly see Apple taking proactive steps to encourage customers to evaluate what they’re putting in.
Nevertheless, is that this a sign of how unhealthy malware is getting on the platform? Perhaps, however it may be a transfer to encourage extra builders to submit apps for notarization.
The info are: In 2023, we witnessed a 50% YoY enhance in new macOS malware households. Moreover, Patrick Wardle, founding father of Goal-See, instructed Moonlock Lab that the variety of new macOS malware specimens elevated by about 100% in 2023 with no indicators of a slowdown. And just some months again, Apple pushed its largest-ever XProtect replace with 74 new Yara detection guidelines.
Regardless, I’ve as soon as introduced this as much as an worker internally and was not met with a lot curiosity. So, I’m glad somebody modified their thoughts, irrespective of the explanation.
Extra: Apple addresses privateness considerations round Notification Heart database in macOS Sequoia
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.

