
Cybersecurity firm FuzzingLabs has accused the Y Combinator-backed startup, Gecko Safety, of replicating its vulnerability disclosures and backdating weblog posts.
In accordance with the corporate, Gecko filed CVEs for 2 vulnerabilities that FuzzingLabs beforehand disclosed, and even “copied the PoCs, re-submitted them, and took the credit score.”
Gecko Safety has denied any wrongdoing, calling the allegations a misunderstanding over disclosure processes.
FuzzingLabs cries foul
A public dispute has erupted between two cybersecurity startups, FuzzingLabs and Gecko Safety, after the previous accused the Y Combinator-backed agency of copying its vulnerability discoveries and claiming credit score for a number of CVE IDs.
“They copied our PoCs, claimed CVE IDs, and even back-dated their weblog posts,” alleges FuzzingLabs on social media.
“This is not nearly two CVEs, it’s about integrity in safety analysis. We observe accountable disclosure. They waited for our public stories, copied the PoCs, re-submitted them, and took the credit score.”
The vulnerabilities being referred to by FuzzingLabs are:
- Ollama (ollama/ollama) server authentication token stealing vulnerability: Authentic report filed Dec twenty fourth 2024. Later assigned CVE-2025-51471.
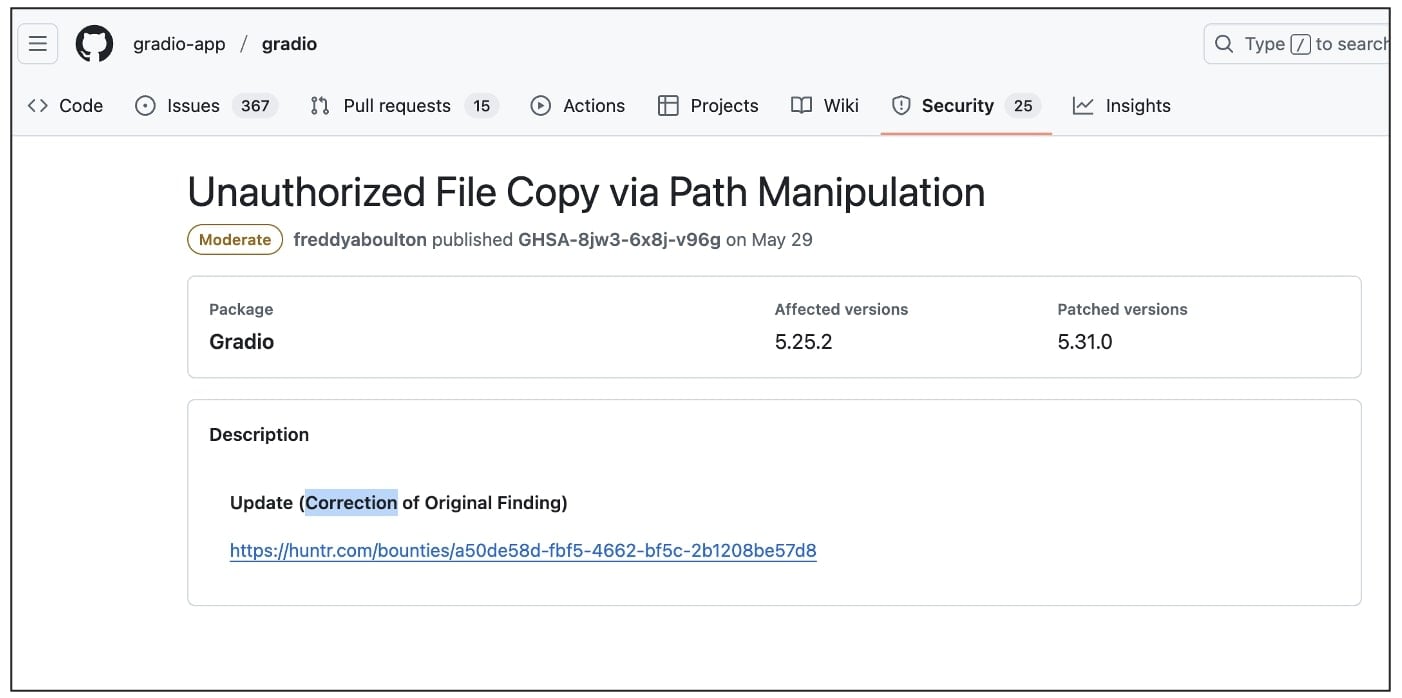
- Gradio (gradio-app/gradio) arbitrary file copy & Denial of Service (DoS) by way of flagging mechanism: Authentic report filed Jan sixteenth 2025. Later assigned CVE-2025-48889.
FuzzingLabs is a research-oriented cybersecurity firm that has developed open-source instruments that leverage AI for offensive safety and fuzzing, essentially the most outstanding being FuzzForge. Gecko touts itself because the ‘AI Safety Engineer to your Codebase’ that helps discover and repair safety vulnerabilities in your codebase.
In its investigation, FuzzingLabs discovered that pull requests (PRs) submitted by Gecko “had been created after our respectable Huntr stories went public” and that some vulnerabilities had a number of CVE IDs, one from their unique hunter.dev report, and one other from Gecko-submitted PRs.
FuzzingLabs additional claims that Gecko backdated its weblog posts to make them seem older than the actual disclosures.
The corporate additionally says it has “indeniable proof” of Gecko copying their exploits line-by-line as a result of these contained “distinctive fingerprints we deliberately inserted to determine our work” within the occasion of plagiarism.
“And it is not simply us, at the very least 7 vulnerabilities on their web site look like stolen from different researchers,” shared FuzzingLabs in the identical thread, referring to their detailed findings with timestamps.
GitHub seems to have up to date some advisories to credit score FuzzingLabs’ unique stories:
Gecko Safety denies wrongdoing, credit researchers
Gecko has since edited its earlier weblog put up(s) crediting FuzzingLabs researchers Mohammed Benhelli and Patrick Ventuzelo, and up to date publishing dates.
Gecko has characterised the scenario as an unlucky overlap, not intentional plagiarism, emphasizing that its workflow entails coordinating straight with challenge maintainers somewhat than by means of third-party platforms.
In a succinct response to social media posts calling out the startup responded:
“Upset to see public accusations with out reaching out first, particularly after launching a aggressive product.
We work straight with maintainers by way of GitHub, not bounty platforms. Neither we nor the maintainers knew about your Huntr stories on the time, in any other case they’d have been marked as duplicates.
We have publicly credited FuzzingLabs for the two CVEs the place your findings got here first, and we’re at all times completely satisfied to credit score whoever finds them earlier than we do.
The declare about stolen CVEs would not maintain up when many hyperlinks you supplied had been already marked as ‘duplicate’ or ‘invalid’ on Huntr.”
Some members of the safety group questioned Gecko’s rationalization, whereas others pointed to the broader challenges of triaging duplicate vulnerability stories, particularly as uncertainty looms over the way forward for CISA’s CVE program.
BleepingComputer reached out to each Fuzzing Labs and Gecko Safety with extra questions on the matter. We didn’t hear again from Gecko.
In an e-mail to us, FuzzingLabs’ Patrick Ventuzelo restated a lot of what the corporate had already outlined on social media, whereas welcoming Gecko’s updates following its posts.
“Nonetheless, the unique sequence of occasions … and back-dated weblog entries raises [sic] broader considerations about their total course of,” Ventuzelo instructed BleepingComputer.
“They’ve referred to those instances as ‘duplicates,’ however having equivalent PoCs and distinctive markers we inserted ourselves straight collides with that narrative.”
The event highlights the nuances of credit score and coordination in accountable vulnerability disclosure, particularly when a number of researchers or corporations could independently determine related flaws throughout totally different platforms or ingest vulnerability information from the online.


